From 21 to 24 October 2025, Cork, Ireland, was once again transformed into a true hacker's paradise. Pwn2Own Ireland 2025, The Trend Micros Zero Day Initiative (ZDI), lured the best security researchers in the world with fat prize money and a very special treat: A million dollars for a WhatsApp exploit.
Spoiler alert: This million remained untouched in the end. More on that right away.
What is Pwn2Own?
If you are wondering: ‘Pwn2Own – what is that please?’ – here is the summary: Pwn2Own is the World Championship for Ethical Hackers. Security researchers from all over the world are coming together and trying to hack live devices that we all use on a daily basis: Smartphones, smart home gadgets, printers, NAS systems and much more.
The special feature: The vulnerabilities they find are not sold on the darknet, but reported directly to manufacturers so that they can patch their products. Everyone gets 90 days to close the gaps before they are made public. Win-win for everyone except cybercriminals.
The figures speak for themselves
After three intense days, Pwn2Own Ireland 2025 came to an end with impressive figures:
- $1.024.750 paid out to prize money
- 73 unique zero-day vulnerabilities discovered
- Dozens of teams from all over the world at the start
For comparison: Last year, more than 70 zero-days were found for $1.07 million. The event in Cork has therefore firmly established itself as THE event for consumer security research.
Day 1: A perfect start
The first day went like clockwork, not a single failed demo! In total, $522,500 for 34 unique bugs poured out. Here are a few highlights:
The SOHO Smashup: $100,000 in one go
Team DDOS with Bongeun Koo and Evangelos Daravigkas showed how it works. They not only cracked one, but two devices in a combo attack: The QNAP Qhora-322 Router and this QNAP TS-453E NAS System. And the best? They used it to write and write. 8 different bugs, Several injections included. This ‘SOHO Smashup’ category exists because many of us work from home and cybercriminals can use precisely these home networks as gateways into corporate networks.
What is an injection? Imagine entering your name on a website. Normally, the system expects something like ‘Max Mustermann’. During an injection, malicious code is smuggled in instead, which is then executed by the system, for example, to get data or to take over the device.
Summary of the livestream ‘Live from Pwn2Own Ireland: STAR Labs targeting the Sonos Era 300’ from the canal Trend Zero Day initiative:
The first stream offers an insight into the first day of the hacker competition Pwn2Own Ireland 2025. Dustin Childs, Head of Threat Awareness, Trend Zero Day Initiative The STAR Labs team shows how to use the smart speaker Sonos Era Successfully exploited.
The team has a total of 30 minutes, divided into three attempts of 10 minutes each Procedure for success: If the exploit succeeds, the team goes to a private room to disclose the vulnerability (Disclosure Room). Subsequently, the producers concerned will be consulted to ask questions.
Result: The attack was successful It was quickly confirmed
Printers, the uninvited guests in the network
Several teams took on printers, virtually the underestimated security risks in every office. STARLabs cracked it Canon imageCLASS MF654Cdw with a heap-based buffer overflow and cashed $20.000.
What is Buffer Overflow? A buffer is like a glass of water. A buffer overflow happens when you try to inject more water than fits in. For software, this means: You stuff more data into a storage area than it can actually process. The excess data ‘swap over’ into adjacent storage areas and if you are skillful, you can take control of the program. In the case of one Heap-based Buffer overflow happens in a dedicated storage area called ‘Heap’, where programs dynamically store data.
Smart home, dumb security?
The Philips Hue Bridge, the smart lighting control of many households, also did not have a good day. Team ANHTUD used four different bugs; including several overflows and an OOB Read around $40.000 bagging.
What is an OOB Read? OOB stands for out-of-bounds. Imagine a bookshelf with 10 compartments. An OOB read is like a program trying to read the 11. Read the book even though it doesn't exist. Instead, it then reads any other data from memory that actually has nothing to look for there. This can often be used to spy on sensitive information.
Day 2: Samsung Galaxy S25 falls
The second day brought more $267,500 for 22 unique zero-days. The absolute highlight:
Samsung Galaxy S25 hacked
Ken Gannon of the Mobile Hacking Lab and Dimitrios Valsamaras of the Summoning Team showed an impressive exploit chain with Five different bugs, to take over the brand new Samsung Galaxy S25. Reward: $50,000 and 5 Master of Pwn Points.
But what exactly did they do? The details are still under lock and key, but such smartphone hacks are often about overcoming multiple security barriers one after the other: First find a bug to be able to execute code at all, then bypass the rights control to get to the system, and finally leverage further protection mechanisms to get full access.
QNAP in the sights
The QNAP TS-453E, a popular network attached storage (NAS) system, has been attacked several times. Particularly clever: Chumy Tsai of CyCraft Technology used a single Code injection, to gain access. In a code injection, malicious code is introduced into a system, which is then executed by the system itself. It would be similar to giving someone a note with an order and the person executes it without questioning whether the order is dangerous.
Synology DS925+ cracked: $20,000 for a bug chain
An outstanding success was achieved Le Trong Phuc (chanze@VRC) and Cao Ngoc Quy (Chino Kafuu) from the team Verichain's Cyber Force. They adopted the popular Network Attached Storage (NAS) system Synology DS925+ In the sights. NAS devices are at the heart of data storage in many households and small businesses, so an attack on them is particularly critical.
The team used a sophisticated Chain of Two Unique Vulnerabilities. This chain included a Authentication bypass.So they were able to bypass the security check and eventually allowed them to execute code with the highest privileges (as root) on the system. For this complex exploit, they received $20.000 Prize money and 4 Master of Pwn Points.
QNAP TS-453E: A single exploit is sufficient for root access
It is also a NAS system that QNAP TS-453E, was made by Chumy Tsai (CyCraft Technology) successfully compromised. Unlike the colleagues at Verichains, Chumy Tsai only needed a single, unique Code injection vulnerability, to crack the device.
This successful proof of the vulnerability has also been $20.000 and 4 Master of Pwn points honored. The successful exploits of the two top brands Synology and QNAP underline the need to: Always update NAS systems in a timely manner, as soon as manufacturer patches are available.
Phillips Hue Bridge: Collision with competition
Successful in the smart home sector Rafal Goryl from PixiePoint Security an exploit of Phillips Hue Bridge, the central control unit for the popular smart lighting systems.
Although the attack was successful, it turned out that the vulnerabilities it used were already present in a Collision with a previous post stood. That means another research team had reported the same gap earlier. Nevertheless, his work was recognized: He received $10.000 and 2 Master of Pwn points.
Day 3: The grand finale
The last day had it all: Achievements, collisions (when multiple teams find the same bug) and the big WhatsApp disappointment.
More Samsung hacking
Interrupt Labs again showed that the Galaxy S25 is not uncrackable. With one Improper Input Validation Bug They took over the device and even activated the camera and location tracking. Again $50.000 and admiration from all sides.
What is Improper Input Validation? Validation means ‘verification’. When an app accepts input (e.g. when you fill out a form), it should check whether the input makes sense and is secure. In the case of ‘improper’ validation, i.e. insufficient validation, the app does not do this correctly. Hackers can then make entries that the program does not expect and thus cause errors that can be exploited.
The printer Olympics
Team Neodyme cracked a Canon printer MF654Cdw with a Integer overflow.
What is an integer overflow? An integer is an integer. Computers store numbers in limited space. Imagine a mechanical odometer in the car that can only count to 99,999 km. What happens if you drive the 100,000th mile? He jumps back to 00,000. This is exactly what happens with an integer overflow, the number becomes so large that it ‘turns over’ and suddenly becomes small again (or negative). Skillful hackers take advantage of this to bypass security mechanisms.
But the absolute highlight? Interrupt Labs Loaded After Their Successful Hack Doom on a Lexmark printer, model CX532adwe.
Yes, you read it right. The legendary video game Doom on the display of a printer. You couldn't play it, but just the fact that it was possible to load this showed full control over the device.
Security cameras are not safe
David Berard of Synacktiv took the Ubiquiti AI Pro Security Camera before and managed to take them over, including, of course, a demonstration with ‘Baby Shark’ on the display. $30.000 for this performance.
An interesting exploit was also presented by namnp from Viettel Cyber Security. He used a crypto bypass + heap overflow against the Phillips Hue Bridge. This brought him $20,000 and 4 Master of Pwn points one.
The elephant in the room: The WhatsApp withdrawer
Let's get to the most exciting part of the whole event: The million-dollar story that didn't turn out to be one.
The prehistory
Meta, the company behind WhatsApp, was co-sponsor of the event and had offered a juicy reward: A million dollars for a zero-click WhatsApp exploit with code execution. Zero-click means: The attack works without the victim having to press a single button or click on a link. These exploits are the premier class because they are the most dangerous.
For comparison: Last year, "only" $300.000 For such an exploit and no one had one. Meta thought to himself: “Okay, maybe the prize money is just too low. Let's make a million out of it!”
What happened to Team Z3?
Team Z3, with a researcher named Eugene, had signed up for exactly this attempt. The whole community waited anxiously. A zero-click WhatsApp exploit would have been absolutely blatant. WhatsApp is used by more than 3 billion people worldwide.
The withdrawer
On the last day, the disappointment: Team Z3 withdrew their submission. No demo, no million dollars, no details. Instead, they decided to clarify their findings directly and privately with Meta's ZDI analysts and engineering team.
What's behind it?
After the event, more details came to light that make the situation more complicated:
According to WhatsApp, the bugs reported by Team Z3 were only minor risks and Cannot be used for code execution. A WhatsApp spokeswoman said: “We are disappointed that Team Z3 withdrew from Pwn2Own because they did not have a functional exploit.”
On the other hand, Eugene of Team Z3 claims that that he had a working exploit and wanted to disclose it privately for personal reasons, Instead of publicly demonstrating at Pwn2Own. He says he wants to protect his identity.
The questions remain
Did Team Z3 have a working million dollar exploit or not? The truth is probably somewhere in between:
- Option 1: They had found interesting bugs, but not a complete zero-click RCE exploit (remote code execution) that would have been worth the million. Maybe they were close, but not close enough.
- Option 2: They had a working exploit, but wanted to go the private way for strategic, personal or business reasons. Maybe to maintain a better relationship with Meta or to position yourself for future bug bounty programs?
- Option 3: The exploit worked partially, but not reliably enough for a live demo under time pressure.
What we know for sure: According to the meta, the two reported bugs were ‘low-risk’, i.e. not particularly dangerous. This suggests that the full exploit, if it existed, was not fully shared, or that it did not exist at all.
Master of Pwn: The Summoning Team triumphs
At the end of the event it was clear: This Summoning team (Sina Kheirkhah, McCaulay Hudson, Dimitrios Valsamaras and Enrique Castillo) won the title ‘Master of Pwn’ of the unofficial World Hackers’ Championship.
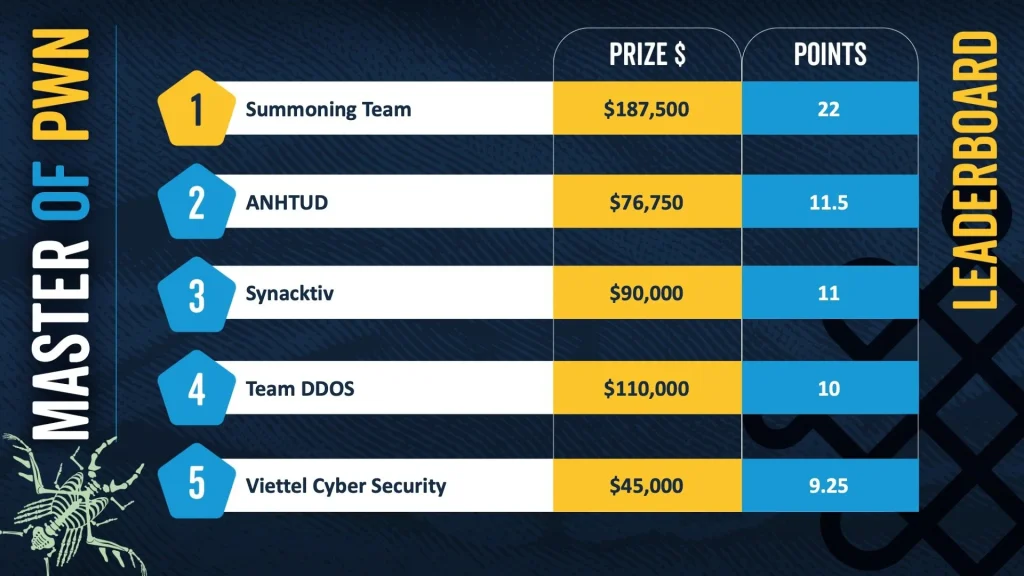
The team scored in several categories:
- Synology devices cracked
- Surveillance cameras adopted
- Smart home systems hacked
- Participated in the Samsung Galaxy S25
Your price? A fancy trophy, a wearable (a kind of special jacket or something like that), and 65,000 ZDI reward points, which means instant platinum status next year.
What does all this mean for us?
The good news: All 73 vulnerabilities found are now patched. Manufacturers have 90 days to release updates before the details become public. This means your devices will be safer. What do you have to do for it? Install the updates.
The bad news: For every gap found at Pwn2Own, there are probably ten others that no one has yet discovered. Or worse: They are already being exploited by cybercriminals.
Important takeaways
For end-users:
- Install updates as they become available
- Regularly update ‘boring’ devices such as printers and NAS systems
- Do not operate smart home devices on the same network as your important computers (if possible)
- For smartphones: The latest models are not automatically safer as the Galaxy S25 has shown
For the tech world:
- Pwn2Own shows that even the big players like Samsung and Meta still have a lot to do
- The million-dollar WhatsApp bounty remains, maybe next time?
- Security is a cat-and-mouse game that never ends
outlook
The next Pwn2Own will take place from 21-23 January 2026 in Tokyo instead. This is about automotive safety. Let's see if anyone can hack a Tesla car there (yes, Tesla is a sponsor again).
Until then: Stay safe, install your updates, and if one day you hear a printer play Baby Shark without you wanting to, you now know that it is not just a ghost in the device, but possibly a security researcher who had his fun.
TL:DR
Total prize money: $1.024.750
Zero-days found: 73
Shopped million-dollar WhatsApp exploits: 0 (unfortunately)
Doom versions played on printers: At least 1
And that was Pwn2Own Ireland 2025, where hackers show that even your ‘smart’ devices are sometimes not as smart as they think.