Again this week there are nine content about which I stumbled, which I feel interesting or important enough to share and as usual you get everything again salted with personal opinion. So let's go straight into week 25.08 - 31.08 (KW35-2025)
Apple/Whatsapp ZeroDay | Citrix Bleed 3 | Google GCUL | Youtube KI VideoMod | Phison Take2 | PayPal blockade | FreePBX attack | Electricity prices | OSBA vs BSI
Article 1
An emergency for Apple users: Zero-Day Attacks and What They Mean
Imagine you're using your phone as usual, and in the background you're being cheered for malicious code without even pressing a single button.
This sounds like a science fiction film, but is unfortunately a bitter reality such as security-insider.de reports. Recently Apple Update: as well as WhatsApp Emergency updates have been released to close such a gap. She was so dangerous because she Actively exploited by attackers became.
What is an Zero-day attack? This is when hackers find and exploit a vulnerability in a piece of software before the manufacturer even knows about it. So the developers had ‘zero days’ to fix the problem. It is a race against time, because as long as the gap is not yet known, there is no protection against it.
Apple closes a dangerous gate
This is a gap that CVE-2025-43300 | EUVD-2025-25409, Apple recently closed with an emergency update. It affected almost all Apple devices – iPhones, iPads and Macs. The problem was in Image I/O Framework, a system library responsible for processing images. Imagine if a manipulated photo could cause hackers to run malicious code on your device and, in the worst case, even the Take full control could.
Apple has iOS 18.6.2, and updates for iPadOS and macOS responded quickly. It's super important that you install these updates immediately, because the gap has already been exploited in attacks.
To protect your devices, make sure they are updated to the following secure versions:
For iPhones and iPads:
- iOS 18.6.2 and iPadOS 18.6.2 (for iPhone XS and newer models, iPad Pro 13-inch, iPad Pro 12.9-inch 3. Generation and newer, iPad Pro 11-inch 1. Generation and newer, iPad Air 3. Generation and newer, iPad 7. Generation and newer and iPad mini 5. generation and newer)
- iPadOS 17.7.10 (for iPad Pro 12.9-inch 2. Generation, iPad Pro 10.5-inch and iPad 6. generation)
For Macs:
- macOS Ventura 13.7.8
- macOS Sonoma 14.7.8
- macOS Sequoia 15.6.1
Update for the weekend:
WhatsApp in the sights: Zero-click attacks on Apple devices
As if that wasn't enough, there were WhatsApp A zero-click vulnerability. The gap CVE-2025-55177 | EUVD-2025-26214, It allowed attackers to install spyware on iPhones and Macs without the user noticing. It was enough if a manipulated message was sent. Since the vulnerability exploited a gap in Apple's Core Image Library, there is also the possibility that attackers have already actively exploited other gateways for exploitation. Whatsapp Security Advisory It is said that the vulnerability is believed to have been used to subjugate malicious code on certain people's devices. Now everyone can interpret what they want, I just leave it that way.
The fatal: This WhatsApp vulnerability could be used in conjunction with the above-mentioned Apple ZeroDay vulnerability. This allowed attackers to access your device and install malicious code via a completely harmless message with a simple manipulated image. Since the two gaps were apparently already actively exploited this week, not only the updates are strongly advised.
What you need to do now
Cyber threats are real, but you can protect yourself. Your top priority should be to keep your devices and apps up to date.
- Update WhatsApp: Check if you have the latest version of WhatsApp. The vulnerable versions were WhatsApp for iOS version 2.25.21.73 or older, WhatsApp Business for iOS version 2.25.21.78 and WhatsApp for Mac version 2.25.21.78 or older.
- Update operating system: Instantly install the latest updates for your iPhone, iPad, and Mac. Just go for it Settings > General > Software update and download the latest version.
- Factory reset if suspected: If you feel your device might be infected, a full factory reset is the safest way to remove the spyware.
In summary, it can be said: These incidents show once again how important it is to stay vigilant and take updates seriously. Apple devices are no longer spared, which is likely to be the 6th or 7th. It was ZeroDay this year. Let's navigate digital life safely together!
Article 2
Around 4,300 vulnerable Citrix Netscaler instances in Germany alone
A new security leak known as Citrix Bleed 3, It's causing a lot of excitement in the IT world right now. Just last month, Citrix Bleed 2 had a similar uproar at the start. Let's see if it's right:
The vulnerability concerns: Citrix NetScaler Systems used by many companies worldwide to manage networks and remote access.
What is Citrix Bleed 3?
Citrix Bleed 3, also known as Identifier CVE-2025-7775 | EUVD-2025-25838, is a critical vulnerability in Citrix NetScaler ADC (Application Delivery Controller) and NetScaler Gateway products. The gap is based on an Memory overflow (memory overflow), which allows attackers to remotely execute unauthenticated malicious code (remote code execution, RCE). In the worst case, they can gain control of the system or cause a complete denial of service (DoS).
Citrix has confirmed, that this vulnerability already as Zero-day-Gap actively exploited before patches were available. This makes the threat particularly acute.
Global reach of attacks
According to scans of Shadowserver Foundation More than 28,000 Citrix systems worldwide are vulnerable to the vulnerability because they have not yet been patched. With more than 4,300 unpatched systems, Germany is particularly affected and ranks second in the world compared to other countries, directly behind the USA.
The Netherlands' NCSC (Nationaal Cyber Security Centrum) has already warned that a Massive exploitation the vulnerability is imminent, as the affected system configurations are very common.
What administrators need to do now
Citrix immediately released security updates. Administrators of affected NetScaler ADC and NetScaler Gateway systems should urgently perform the following steps:
- Patching: Install the patches provided to update the systems to the secure versions. Affected versions include: NetScaler ADC and NetScaler Gateway 14.1, 13.1 and the FIPS and NDcPP versions of 13.1 and 12.1, which have not reached the recommended patch levels.
- Check systems for compromise: This NCSC has released a script on GitHub, which was originally developed for a previous vulnerability, but can also be used to check for successful attacks by Citrix Bleed 3.
The quick response of the admins is crucial to protect their systems and the associated data from cybercriminals.
Article 3
Google is serious: Own blockchain for the financial world goes into test phase
The tech giants are taking blockchain technology more and more seriously – and now Google Cloud is also heavily involved.
As it became known this week, the company has its own Layer 1 blockchain named Google Cloud Universal Ledger (GCUL) Announced at the beginning of the year, it has now been launched in a private testing phase. This officially brings Google a big step closer to the playing field of the blockchain infrastructure and also directly targets the global financial world.
What is GCUL?
GCUL is a powerful, trust-neutral blockchain platform designed specifically for the stringent requirements of financial institutions. The special thing about it: The Smart Contracts of the Blockchain will be implemented in the popular programming language Python written. For thousands of developers already familiar with Python, this significantly lowers the entry barrier to blockchain development.
The strategy behind the blockchain
Google is deliberately positioning its blockchain as Neutral infrastructure. This is clever, because financial companies are traditionally very reserved when it comes to building on the proprietary blockchain of a direct competitor. With GCUL, Google wants to create a common, trustworthy foundation on which each financial institution can safely develop its own applications. This neutral role is already known from Google Cloud itself, which has established itself as a provider of infrastructure services for various companies.
Google's move is part of a bigger trend. More and more large players such as Tether, Stripe and Circle have recognized the importance of controlling their own basic blockchain layer (layer-1).
A milestone for the Web3
The revelation of GCUL is the result of years of secret research and development. Google has kept the project under wraps for a long time, but now publicly acknowledges its existence. Industry observers are eagerly awaiting the release of further technical details to better assess the exact architecture and capabilities of the blockchain.
The strategy behind the blockchain: neutrality
Google deliberately positions GCUL as ‘credibly neutral’ Base layer. In the financial world, competitors rarely build applications on rivals' proprietary systems. Google uses its established role as a neutral cloud provider to create a common infrastructure on which each institution can safely build without falling into a competitor’s ecosystem.
This is also reflected in the first pilot projects: The CME Group We are already testing with Google Cloud. tokenisation of assets and wholesale payments. Additional market participants are to be added gradually.
Criticism from the crypto world: “Permissioned is not decentralised”
Although Google is talking about a blockchain, GCUL has a ‘permissioned’character. This means that not everyone can participate in the network; the actors need to be authorised, in line with the compliance and strict regulatory requirements of financial institutions.
In the crypto community, this is met with skepticism. The main allegation is: ‘Permissioned is not decentralised.’ GCUL is therefore used by critics rather than Consortium ledger This is because it is classified as a ‘real’ public blockchain such as Bitcoin or Ethereum. While this model offers benefits such as lower operational risks and predictable fees, it requires confidence in operator governance and transparency that Google still needs to deliver.
Nevertheless, GCUL could be a sensible solution for financial institutions. The focus on Compliance, easy integration via API and the use of Python makes the platform attractive to the regulated sector. It's not so much about open crypto-ecosystems as it is about open crypto-ecosystems. modernisation Existing financial processes.
The success of the project will depend on whether Google provides the necessary transparency for governance and interoperability and the financial world accepts the offer. However, one thing is clear: With a focus on financial institutions and a neutral approach, GCUL could challenge existing Layer 1 solutions in the crypto industry and drive the mass adoption of blockchain technology in traditional finance.
Article 4
AI on YouTube: Hidden video editing?
Hey guys, have you ever felt like there's something wrong with your favorite videos on YouTube?
Suddenly faces seem a bit weird, hairstyles look strange or the skin tones are somehow shifted? You are not alone! It seems as if an invisible hand blends into the videos, but this hand belongs to Artificial intelligence (AI).
What's behind it?
As the BBC recently revealed, YouTube has secretly used AI tools to rewrite video content. The whole thing happened without authors or uploaders being informed about it. Only when more and more users complained about strange distortions in the comments and in their own videos did YouTube finally admit to experimenting with the technology.
A spokesperson said the goal was to reduce blurring and image noise, much like modern smartphones do automatically. But sometimes the results are far from perfect. Instead of improving the videos, AI creates bizarre alienations that quickly turn an authentic video into a ‘degenerated’ or ‘AI-generated’ piece. And the (in my opinion) most frustrating thing about the situation: Uploaders do not seem to be able to contradict these interventions. Very big cinema.
A contradiction in itself?
YouTube had only announced in autumn 2023 that creators would have to label their own AI-generated content if it seemed realistic. This is especially true of videos that show people saying or doing something they have never done in reality. But the clandestine post-processing of already published videos by YouTube itself is in stark contrast to this rule.
It is a matter of transparency and trust. When YouTube asks its users to be open about the use of AI, they should lead by example themselves. Or am I the only one who sees that?
It's not even important to me that the landlord is allowed to do things that the guest is not allowed to do. Also Quod licet Iovi, non licet bovi So I see measuring with double standards, even if it is morally questionable.
Many reacted similarly annoyed when the automatic AI translation was activated unasked for selected videos, which worked really badly in the beginning. Please leave the content as intended by the creator, instead of trying to smear it.
Conclusion: What does this mean for us?
Whether a strange hairstyle or a false skin tone can be business-damaging is questionable, but the thing is clear: It's about authenticity. I lean out of the window and claim all uploaders attach great importance to presenting their content as unadulterated as possible. If YouTube secretly makes changes, that trust will be damaged.
What do you think about it? Do you think it is okay that YouTube ‘improves’ videos in the background, especially at the risk of making them worse? I think it should be a no-go.
Article 5
SSD failures and Phison controllers: An addendum to the ‘hot topic’
Last week Reports of SSD failures with Phison controllers caused unrest among many PC users. Since there was not much durable information was also speculated accordingly wild.
The problem seemed to occur suddenly and without warning, and initial speculation suggested an unfortunate combination of the latest Windows updates and high write load on well-filled drives. But the case takes an unexpected turn: The manufacturer Phison himself can be the problem in spite of intensive internal tests Do not re-enact, how the company announces to wccftech.com.
Update for the weekend: Microsoft also Looks for investigations There is no error as a cause could be eligible. Joah, that's stupid.
The search for the needle in the haystack
The mystery of why some users experience problems and others don't, leaves Phison's experts with a big question mark. They tried to reproduce the problem under different conditions, with different hardware configurations and under high stress, but without success. The affected users mainly reported failures that occurred after the installation of the recent Windows updates, often under the conditions of intense write load, while the SSD was already heavily filled.
Heat as a potential catalyst?
Speculation goes further, and Phison himself has brought an interesting theory into play: The role of cooling. The suspicion is that the high temperatures prevailing in July and August may have favored the cause of the failures. The assumption is that a Microsoft patch changed the memory mechanics of the controllers, resulting in increased operating temperature. If this change occurs in combination with already high ambient temperatures, the controller could "sweat" and, in the worst case, fail.
Wild guess on my part: Could something have been changed in the Microsoft patches KB5063878 and KB5062660, which ultimately brings the thermal throttling of the controller out of sync? Thermal throttling is an automatic protection mechanism in computers and other devices that reduces the performance of a processor or other components when they reach a critical operating temperature.
This scenario would explain why the outages occurred only to a certain group of users and why Phison was unable to replicate the problem in his labs (which are likely to work under controlled, cooler conditions). Update: Microsoft had a weekend. also in his admin portal He spoke and also said:Nothing found„.
Whether this is a chain of unfortunate circumstances or a fundamental problem that only becomes visible under extreme conditions remains to be seen. However, it shows once again how complex the interaction between software updates, hardware components and environmental factors can be.
Update for the update, Sunday afternoon:
Even though everyone says it's nothing, there is now a Youtuber who was able to reproduce the problem (though not as originally described) but obviously with the same effects during his last video creation.
Well, so everything back to the beginning. We haven't imagined it, even if everyone involved says otherwise.
Interim solution as of Sunday:
Windows Updates KB5063878 and KB5062660 can probably only be uninstalled without an error message if you deactivate the Windows Sandbox feature beforehand. There is also information from another Youtuber:
You can then activate the sandbox feature again as far as I have read.
The two updates I would (if you use NvME with Phison Controller and are affected yourself) uninstall and then either temporarily suspend your Windows updates, which is not ideal, or use e.g. the Powershell (start as admin) from the Windows Updates catalog for your system at least for the moment to hide the two problem bears after uninstalling KB5063878 and KB5062660. How that goes is nicely described here:
# Install the PSWindowsUpdate module (run with administrator privileges) Install modules -Name PSWindowsUpdate -Force -SkipPublisherCheck # Import the module Import Modules PSWindowsUpdate # Search for available updates (takes some time) $updates = Get-WindowsUpdate # Display all available updates (to find the ID of the update to be blocked) $updates ⁇ Format-Table -AutoSize # Suppose the update to be blocked has the ID KB5063878 $updateID = "KB5063878" # Hide the specific update Hide-WindowsUpdate -KBArticleID KB5063878 -Verbose # Check if the update was hidden Get-WindowsUpdate -IsHiddenShould look like this: (Habs fixed times clicked through on a test system with me)
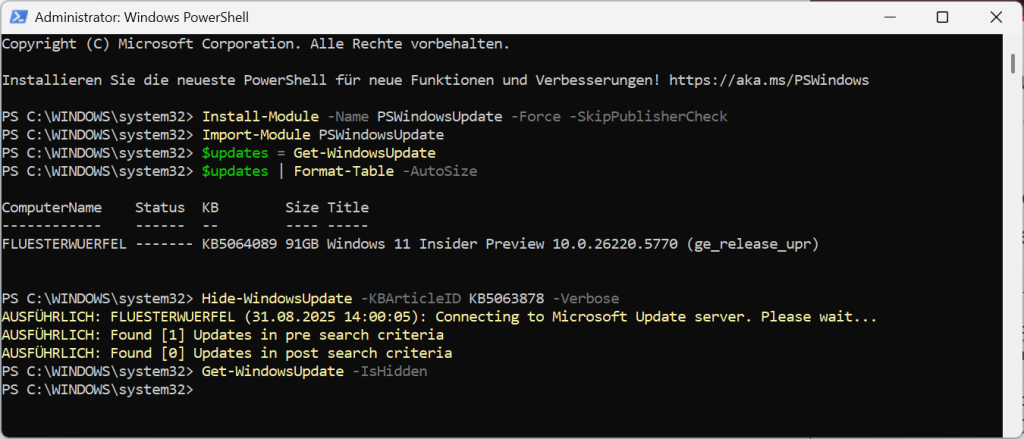
If there is a fix in the next few weeks and the update is either withdrawn or replaced by a new one, you just have to install the new updates normally and have your peace of mind. But if you want to show the hidden update again for whatever reason, you can use this command:
#Start the Powershell again as an administrator # Shows update KB5063878 again, others then adjust according to number Show-WindowsUpdate -KBArticleID KB5063878 -Verbose # Check if it is no longer hidden: (then reappears in the list) Get-WindowsUpdate -IsHiddenArticle 6
PayPal in payment jam: System failure in security systems causes chaos
Many users in Germany are currently experiencing massive problems when paying with PayPal. The reason for this is a serious failure in an internal security system of the US group.
The result: Some German banks block direct debits on a large scale to protect their customers from fraud. But let's start first.
What happened?
How Many media reports, PayPal is a system for Fraud detection It's supposed to filter out suspicious transactions. Because this system did not work in whole or in part over the past weekend, direct debits were carried out without the usual security check.
As a result, the security systems of several German banks jumped on over the weekend until the beginning of the week. In order to prevent fraudsters from unlawfully debiting large amounts, banks such as Bayerische Landesbank and DZ Bank, which handle payments for cooperative banks, have blocked PayPal's direct debits.
Massive impact for users and retailers
The chaos has far-reaching consequences:
- Payment problems: Many users are currently unable to pay with PayPal.
- Cancelled orders: Since merchants do not receive any money, many orders have already been cancelled.
- Multi-billion dollar damage: It is estimated that payments worth more than 10 billion euros be affected. The Bayerische Landesbank alone is said to have frozen around four billion euros.
PayPal confirmed the incident in the support section of its website, referring to a ‘temporary service interruption’ that delayed transactions ‘for a small number of accounts’. Allegedly, the problem has been fixed, but the blockade of the banks continues for the time being. The text is beautiful unobtrusive on the German help side placed in black on grey as an inconspicuous bar with this wording:
Over the weekend, there was a temporary service interruption that may have resulted in a failed bank transaction for some accounts. This problem has now been fixed.
Guys, let's face it. You can do it better! The situation shows how much trust between payment services and banks depends on functioning security systems. How things are going now and when the payments will run smoothly again remains to be seen. The Consumer Centre It also dealt with the incident and possible problems resulting from it.
Stiftung Warentest goes one step further and recommends that the Change password and set up 2FA/MFA, as there have also been recent reports of elapsed access data.
However, whether this data was actually lost at Paypal, or whether many people were simply too lazy to use different passwords and email accounts for different services remains questionable. The technology behind it is called Credential stuffing. Everyone who wants to use the Internet should be required to read. I have to Also an article for you!
Update: Just in time for the weekend, a few politicians can once again stand out, argue nicely with the concentrated ignorance and – Because it just belongs to the good tone – unreflectively call for several independent, European alternative solutions. Now German banks are best to invest in a new, secure, independent system that after 5, no, better still after 10 years of development time was planned to death by dozens of expert committees and later on on the market because of non-existent basic functions no one wants to touch even with the barbecue pliers.
How? Have/have we already? I almost never heard of it, sorry. I don't know anyone who uses it either. Hello to Wero, Giropay/Paydirect and Kwitt ⁇
Hold my beer, i have an idea: It is best to open an EU funding pot, then throw in half a billion euros, because we know that much helps a lot. For the pot, we get a handful of consulting companies to skim off and implement SAP and Siemens as a management duo. Okay, and the Gematik as SME has to be on board to really make sure that the fifth wheel on the car is overengineered from scratch with German engineering by at least a factor of 10. That has to be something.
Fully comfortable, with specially developed Siemens-Nixdorf Tan-Listen printer in trendy grey/turquoise! YAY!
Let me give you the XKCD 927, just for the slow effect:

Article 7
Attack on FreePBX: Is your VoIP telephone system in danger?
If you use FreePBX for business telephony, be careful now!
The popular open source platform, which allows thousands of companies to run their own VoIP system, is currently facing a wave of cyberattacks. The Sangoma Security Team, The developers behind FreePBX sounded the alarm.
What is FreePBX?
Think of FreePBX as a free, dedicated ‘telephone company’ for a company. It is based on the powerful telephone system asterisk, but makes its complex setup with a simple, graphical web interface child's play. This makes it easy to manage internal calls between employees, set up mailboxes, control call forwarding and all this without expensive monthly fees. It is cost-effective, flexible and grows effortlessly with business as well.
The current threat
The problem: Systems whose Administration interface (ACP) is unprotected on the Internet, are at risk. Attackers exploit a vulnerability to gain access. According to Sangoma, a patch is in the works, but until then, users will have to take action themselves.
The most urgent recommendation is: Shut down your FreePBX installation immediately!
What you need to do now
- Restrict access: Use this FreePBX Firewall Module, to restrict access to the admin interface only to trusted IP addresses, ideally only to your own. Disables access via the Internet/External zone for web management.
- Module updates: Checks whether the endpoint module is installed. If so, you should update it to the latest version immediately. For FreePBX users of versions 16 and 17, there is already a ‘EDGE’-Fixed.
- Do you have a suspicion of infection? Search system logs for suspicious signs, such as:
- The admin interface does not load properly or is broken.
- The file
/var/www/html/.clean.shexists (this should not normally be present). - Search Apache logs for POST requests
modular.php. - Search the Asterisk logs for calls to the direct line 9998.
- Check the MariaDB/MySQL database for suspicious new users in the ampusersTable.
What to do in the event of an infestation?
Stay calm. Patch is in the works. Until then, the security team advises the following:
- Securing your data: Back up your backups from before 21 August on an external medium.
- Reinstallation: Installs the system from scratch, directly with a properly configured firewall module and the updated endpoint module.
- Restoration: Restore your system with the backed up backup.
- Change passwords: Changes immediately all Passwords – for the system, SIP trunks, users, mailboxes, etc.
Update: It is now known that Only versions 16 and 17 are affected. If you are still 15, you should be spared this time.
Particularly important: Check yours too Telephone bill! Crowds of unauthorized calls, especially expensive international connections, are a common sign of a successful attack.
If, for whatever reason, you don't have up-to-date backups, manual cleanup is possible, but it's risky. This approach is also discussed in the FreePBX Forum. But keep in mind: Reinstalling is the safest way to regain full control of your systems.
Trade now and protect your FreePBX system!
Article 8
Electricity price relief is likely to fall far short of expectations.
Not only do we in Germany pay the highest electricity prices in an international comparison, we also continue to have a general structural problem of network charges and additional levies.
Current news suggests that the federal government's planned electricity price reform, which is to take effect from 2026, could be disappointing for many households in Germany. Although the government promises to cut prices, the actual expected reliefs are small.
The government's plans in August 2025
The Federal Government plans the following measures to reduce electricity prices:
- Abolition of the gas storage levy: From 1 January 2026, this surcharge, which increases gas and thus indirectly the price of electricity, is to be abolished.
- Permanent reduction of electricity tax: The already reduced electricity tax should remain at the EU minimum level in the long term in order to relieve consumers.
- Reimbursement of network charges: With a subsidy of 6.5 billion euros, the federal government wants to take over part of the network fees. This is the central point of the reform.
But here is the disappointment: Instead of the initially promised reduction of at least five cents per kilowatt-hour, households could only be relieved of maximum 1.5 cents per kWh feel. This is because the federal government bears only part of the costs and network charges remain high.
Why are electricity prices so high in Germany?
Germany has the highest electricity prices in international comparison. There are several reasons for this:
- High levies and taxes: About half of the electricity price is made up of taxes, levies and levies. Despite the planned reform, these burdens remain very high by international standards.
- High network charges: The costs for the expansion and maintenance of the electricity grid are extremely high in Germany. The conversion of fossil energies to renewable energies Like wind and solar energy, massive grid expansion is required to transport electricity from wind-rich north to the industrial south. These costs are passed on to consumers via network charges.
- Global political situation: Geopolitical tensions and the Russian attack on Ukraine have exacerbated the energy crisis. Although wholesale electricity prices have fallen since then, consumers are feeling the aftermath of the crisis in the form of higher long-term prices. Uncertainty in global energy markets remains a price driver.
International comparison
A look at other countries shows how much the German electricity price is influenced by these factors. While countries like the USA or China benefit from significantly lower prices, as they rely on fossil fuels and a different tax structure, European neighbours also pay high prices, but rarely as much as in Germany. For example, countries with a high share of nuclear power, such as France, or a well-developed hydropower network, such as: Norway, tends to lower prices for end-users. The German energy transition, as important as it is for climate protection, is being transferred directly to consumers through the high costs of grid expansion and the integration of renewable energies, which is driving up prices.
Outlook for the future
Experts see electricity prices in Germany at a high level beyond 2026. The planned reform is only a first step, but not a lasting solution to the structural problems. Without a fundamental revision of the costs of network charges and levies, electricity will continue to be more expensive in Germany than in many other industrialised nations.
No? Yes, of course! Oooohhhh…
Article 9
Rethinking Digital Sovereignty: Why the BSI President warns against the ‘digital iron curtain’
The term ‘digital sovereignty’ is on everyone’s lips when it comes to Europe’s future in the global technology landscape. He describes the desire to be independent of external powers.
Recently, the BSI has also been Open Source Business Alliance in an open letter confronted with it. Although the trigger was a statement misrepresented by the DPA, the core of the criticism has a hand and a foot. BSI President Claudia Plattner In a remarkable critique warned against misunderstanding this term. She argues that a purely national, isolationist strategy is not only unrealistic, but also dangerous. Their wake-up call calls for a radical change of perspective: Away from the ‘digital iron curtain’ towards a ‘digital capacity to act’.
In the open letter, the Open Source Business Alliance (OSBA) contradicts the view that Germany must remain dependent on foreign technologies. You emphasise that: Digital sovereignty achievable is. The OSBA criticises Plattner’s ‘suppressive dependence’ and the argument of the Investment advantage of US companies, That they are pure Marketing narrative denoted.
In OSBA's view, this narrative often serves as an excuse for policymakers to delay necessary decisions about sourcing and investing in European solutions. The letter makes it clear: Many dependencies could be reduced in the short term if European policy Open source solutions would specifically take into account and promote them in their calls for tenders. The letter is also supported by over 60 organizations, companies and individuals from the open source environment.
The problem of national isolation
The traditional idea of digital sovereignty is often shaped by the idea that we have to develop and produce all technological components, from chips to operating systems to software ourselves. This is the only way we can protect ourselves from surveillance and foreign interference. But Claudia Plattner considers this vision to be a naïve illusion. She stresses that in a globalised and interconnected world, it is simply impossible to create all the necessary technologies in isolation.
Such an approach would not make Germany and Europe more independent, but rather weaker. We would voluntarily cut ourselves off from the global innovation cycle and push into a digital niche where our own systems would not only be less powerful, but paradoxically also less secure. The development and maintenance of a completely own IT infrastructure would devour enormous resources that could be used much more effectively elsewhere, for example in strengthening cybersecurity.
What True Digital Sovereignty Really Means
For the head of the BSI, digital sovereignty is not a question of total self-sufficiency, but of Ability to act. It's not about owning everything, it's about owning everything. Freedom to make your own decisions. This ability to control autonomously depends on three main factors:
- Understanding: We need to be able to understand the technologies we use. This requires investment in education and expertise to identify and assess dependencies.
- Freedom of choice: True sovereignty means being able to choose from a variety of providers and solutions. A monopoly position – whether from foreign or domestic suppliers – contradicts this principle.
- Resilience: We need to build systems that remain functional even in the event of disruptions, whether caused by cyberattacks or geopolitical conflicts.
From this perspective, it becomes clear that it does not matter whether a server is located in Germany or in the USA, but whether we are able to change providers if necessary and ensure the security of our data. Sovereignty is not a state, but an ability.
The future lies in collaboration, not isolation.
A central point of Plattner's plea that as Answer also on the BSI page as PDF What has been published is the need for international partnerships. Instead of distinguishing ourselves from other countries, we should seek and strengthen cooperation with trusted partners such as the USA, Great Britain and other European countries. Together, we can better address cyber threats and promote open standards that make us less dependent on individual corporations.
Such a collaborative approach allows us to learn from each other, share best practices and form a common front against cybercrime and state actors. This is the only way to protect our collective digital security and Ability to act in a globalized world.
Plattner's criticism is an important wake-up call that takes the debate about digital sovereignty to a new, more pragmatic level. It calls on us to pursue a realistic and forward-looking strategy that does not rely on isolation, but on competence, freedom of choice and international cooperation. At the same time, it invites OSBA stakeholders to engage in dialogue in order to pursue the common goal: Germany and Europe digitally
to make sure, sovereign and successful.
n1 Mrs. Plattner, good answer!
And of course, this week of the honorable ISO 27001 safety lead auditor SunTsu should not be missing:
Adaptability is the key to survival! The IT landscape is constantly changing. Be ready to quickly adapt your strategies and technologies to stay relevant and face new threats. Those who adhere rigidly to old methods will fail.