The news week ends, my nine of them from week 18.8 – 24.8 (KW34-2025) for you in the fast run. As usual seasoned with a little bit of opinion, my ‘wews of the week’:
Libarchive gap | SD in LibreOffice | Phison VS Windows | Thunderbird&Firefox | Customs on Gamescom | Apple Zero Day | BND Recruiting | Intel Trump deal | German digital independence
Article 1
Let's start the week with a paradox where less is more!
The decline in jobs in the IT sector is intensifying – but the shortage of skilled workers remains, at least according to the current IW Cologne survey
In the German IT sector, there was a significant decline in job vacancies between 2023 and 2024. The demand for IT personnel has fallen by 26.2 percent overall. This decline affects particularly highly qualified experts with a master's or diploma degree. For them, the number of vacancies fell by 33.7 percent.
This is, among other things, a consequence of the weak economy and the associated reluctance of companies to invest in innovative projects.
By contrast, in 56 sectors, i.e. the vast majority, the number of vacancies for IT workers has recently decreased. The largest decline is seen in the information technology services sector, which accounts for the largest share of IT professionals (40.9 %). On an annual average in 2024, this
Area 5,821 vacancies less advertised than in the previous year – a decrease of 31.6 per cent. IT experts were particularly affected. Possible reasons for the decline could be that companies are increasingly shifting IT skills that were previously provided by external service providers to their own companies or abroad. Also an
The ‘manufacture of motor vehicles and parts of motor vehicles’ showed a significant decline in the number of vacancies for qualified IT workers. Between 2023 and 2024, the number of vacancies fell by more than a third (down 36.8%) to around 2,000 vacancies. This reflects the current crisis in the automotive industry.
Although the IT sector is shrinking overall, there are exceptions. In the Legal and tax advice For example, the number of vacancies for IT professionals has increased by over 500 percent, as new digital solutions are increasingly being used.
Despite the decline, the shortage of skilled workers in the IT industry continues to be noticeable. On average, more than 13,500 vacancies could not be filled in 2024. The IW-Short Report No. 73/2025 mentions as a reference for this assessment Another own publication Looking forward to 2028.
Computer science experts in particular are in high demand: For them, seven out of ten posts could not be filled. The filling of IT positions therefore remains a major challenge for companies. In the future, the need for IT forces could even increase again, as advancing digitization and the use of artificial intelligence (AI) are changing the requirements for skilled workers and are more likely to play a complementary role.
Article 2
Stable Diffusion for LibreOffice: AI image generation for everyone
A new volunteer-developed extension called ‘Stable Diffusion for LibreOffice’ allows users of the free Office suite (version 7.4) to create AI-generated images directly in Writer and Impress.
Unlike many commercial solutions, this service is free of charge and only requires the installation of the extension and the application for a free, pseudonymous API key.
How it works: The expansion uses the infrastructure of AI Horde, A decentralized crowdsourcing project. Volunteers provide their computing power, mainly from powerful graphics cards (GPUs).
The speed of image generation depends on the utilization of the network. The system operates with an internal currency called ‘Kudos’: Those who contribute computing power or evaluate images receive kudos and are preferred when processing their orders. Users without Kudos may have to wait longer, but can still use the service.
Registration for a key does not require personal information such as names or email addresses.
Important information and additions:
- Other planned integrations: Developer Igor Támara is working on making the extension available for Calc spreadsheet and Draw.
- Other AI plugins: The Stable Diffusion extension is not the only AI tool for LibreOffice. There are also plugins such as ‘localwriter’, which provides generative AI functions for texts running on the user’s own computer, which increases data security.
- Data protection notice: Since the orders for image generation are transferred to the computers of anonymous volunteers, the developer advises against making sensitive or private image requests.
- Free and decentralized philosophy: The existence and functioning of the stable diffusion plug-in and the AI Horde network are consistent with LibreOffice's open source thinking, as they provide free, freely accessible AI tools that are not controlled by a single company.
Article 3
Windows Update KB5063878 causes SSD problems with disks with various Phison controller chips
Again, it has a Windows Update that could have been corrected in the preview with error messages of the users, through the quality check and now causes worldwide frustration.
Some users of Windows 11 are currently reporting Problems with SSDs, which occur in conjunction with the latest cumulative update (KB5063878). Particular attention is paid to drives with Phison controllers.
The cause of the problem
Difficulties arise above all for intensive writing operations For example, when transferring large files or installing games. Various information can be found on the net, but it seems to be agreed that the problem arises from write operations of 50 GB of data. In such situations, there may be an overload of the write cache, which then either causes the SSD to become invisible to the operating system or even shows the data structure as corrupted (RAW).
According to the previous analysis, the error does not lie primarily with the SSDs themselves, but in an interaction of a Windows update and the firmware of certain controllers. A faulty memory management of the operating system causes the I/O queues to be overloaded, after which the SSD controller goes into a faulty state and no longer responds.
Models concerned:
Unfortunately, the data situation so far is not entirely clear. It may also be circulating False information on the net, Phison is already taking action. Mostly, however, SSDs with the Phison controller seem to PS5012-E12 to be affected. Since Phison sells its controllers to numerous major manufacturers (such as Corsair, KIOXIA or SanDisk), the problems are not limited to a single brand. I had read that about various controllers Phison up to 40% The SSD market.
Update 24.8, 21:00h
On Winfuture.com Here is some more information about the technical background of the problem: It is assumed that the last Windows update makes a change to the memory stack, which now leads to buffering problems. The OS thus keeps too much data in the buffer while the kernel handles the flush order incorrectly. Drives up to 60% or more filled are preceded by affected because there the SLC cache is smaller and thus less free blocks are available.
The list of affected SSDs has also been revised: Corsair Force MP600 or all SSDs with Phison PS5012-E12 controller, Kioxia Exceria Plus G4, Fikwot FN955, SSD with InnoGrit controller, Maxio SSD, Kioxia M.2 SSD, SanDisk Extreme Pro M.2 NVMe 3D
How to avoid the problem
Since the cause lies in the interaction between the Windows update and the SSD firmware, there is currently no one hundred percent secure solution, but some important steps to minimise risk:
- Avoid large writes: If you are using one of the potentially affected SSDs, avoid large data transfers (50 GB+) such as installing large games or editing large video files. If possible, carry out such operations in smaller steps.
- Create backups: The most important thing is to make regular backups of your data. So you are at least on the safe side before data loss if your SSD fails.
- Check manufacturer's firmware updates: The responsibility for firmware correction lies with the individual SSD manufacturers who use Phison's reference designs. Keep an eye on your SSD manufacturer's support websites and install all provided firmware updates as they become available.
- Uninstall Windows Update (last option): If the problem has already occurred and there is no other solution, uninstalling the Windows update in question can be a temporary measure. Alternatively, this update can also be temporarily hidden until a corrected version is delivered.
- Has your SSD been affected? Some users also reported data loss observed in this context after a crash. In this case, the problem can be expressed, for example, by the fact that suddenly installed programs can no longer be found, even links to data or apps run into the ‘empty’ as if they had never been installed. Unfortunately, there are already reports of complete failure of individual SSDs.
Both Microsoft as Phison as well The reports have confirmed the problem and at least Phison is already working on a solution. Caution remains to be exercised until an official, broad-based correction is published. Unfortunately, little was heard from the Microsoft camp about this topic this week.
Especially frustrating seems to be that there have already been reports from Japan last month about the problem, the preview update to KB5063878 with the number KB5062660 already seems to cause the same problem. At least the problematic changes have already been rolled out locally there and yet the update package has now been rolled out globally in August. This would have been avoidable.
Updates from the KW35 on the problem:
Attention, just my opinion: Heat as a potential catalyst?
Speculation goes further, and Phison himself has brought an interesting theory into play: The role of cooling. The suspicion is that the high temperatures prevailing in July and August may have favored the cause of the failures. The assumption is that a Microsoft patch changed the memory mechanics of the controllers, resulting in increased operating temperature. If this change occurs in combination with already high ambient temperatures, the controller could "sweat" and, in the worst case, fail.
Wild guess on my part: Could something have been changed in the Microsoft patches KB5063878 and KB5062660, which ultimately brings the thermal throttling of the controller out of sync? Thermal throttling is an automatic protection mechanism in computers and other devices that reduces the performance of a processor or other components when they reach a critical operating temperature.
This scenario would explain why the outages occurred only to a certain group of users and why Phison was unable to replicate the problem in his labs (which are likely to work under controlled, cooler conditions). Update: Microsoft had a weekend. also in his admin portal He spoke and also said:Nothing found„.
Whether this is a chain of unfortunate circumstances or a fundamental problem that only becomes visible under extreme conditions remains to be seen. However, it shows once again how complex the interaction between software updates, hardware components and environmental factors can be.
Update for the update, Sunday afternoon, 31.08:
Even though everyone says it's nothing, there is now a Youtuber who was able to reproduce the problem (though not as originally described) but obviously with the same effects during his last video creation.
Well, so everything back to the beginning. We haven't imagined it, even if everyone involved says otherwise.
Interim solution as of Sunday 31.08:
Windows Updates KB5063878 and KB5062660 can probably only be uninstalled without an error message if you deactivate the Windows Sandbox feature beforehand. There is also information from another Youtuber:
You can then activate the sandbox feature again as far as I have read.
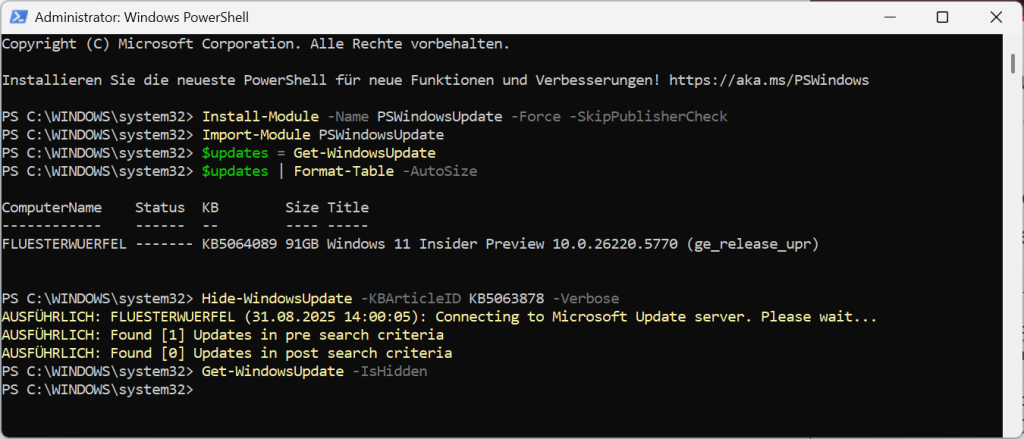
The two updates I would (if you use NvME with Phison Controller and are affected yourself) either temporarily suspend or, for example, hide the Powershell (start as admin) from the Windows Updates catalog for your system. How that goes is nicely described here:
# Install the PSWindowsUpdate module (run with administrator privileges) Install modules -Name PSWindowsUpdate -Force -SkipPublisherCheck # Import the module Import Modules PSWindowsUpdate # Search for available updates (takes some time) $updates = Get-WindowsUpdate # Display all available updates (to find the ID of the update to be blocked) $updates ⁇ Format-Table -AutoSize # Suppose the update to be blocked has the ID KB5063878 $updateID = "KB5063878" # Hide the specific update Hide-WindowsUpdate -KBArticleID KB5063878 -Verbose # Check if the update was hidden Get-WindowsUpdate -IsHiddenShould look like this: (Habs fixed times clicked through on a test system with me)
Article 4
Please install Firefox and Thunderbird updates as quickly as possible
The Mozilla Foundation released important security updates for its popular Firefox and Thunderbird applications on August 19, 2025.
Critical security vulnerabilities in Firefox and Thunderbird: Immediate updates required. These updates close several critical vulnerabilities that could allow attackers to execute malicious code on affected systems.
What happened?
Mozilla has identified and fixed several serious vulnerabilities in various versions of Firefox and Thunderbird. The vulnerabilities affect both desktop versions and Firefox for iOS. It is particularly problematic that some of these gaps have been classified as ‘high’.
Affected versions and updates
Users should immediately upgrade to the following secure versions:
Firefox:
- Firefox 142
- Firefox ESR 115.27
- Firefox ESR 128.14
- Firefox ESR 140.2
- Firefox for iOS 142
Thunderbird:
- Thunderbird 128.14
- Thunderbird 140.2
- Thunderbird 142
The critical weaknesses in detail
CVE-2025-9179: Sandbox escape (threat level: High)
A particularly dangerous vulnerability allows attackers to break out of the sandbox due to memory corruption in the audio/video GMP component. This vulnerability affects both Firefox and Thunderbird and could allow cybercriminals to gain advanced system access.
CVE-2025-9185: Memory error (threat level: High)
Other memory errors can cause malicious code to reach systems, which usually leads to complete compromise of the affected computer. This vulnerability was discovered by Mozilla’s own fuzzing team.
CVE-2025-55032: XSS attacks on iOS (threat level: High)
Especially for iOS users, there is a risk of cross-site scripting attacks that could endanger sensitive data.
Other weaknesses
Additionally, vulnerabilities such as CVE-2025-9180 (same-origin policy bypass) and CVE-2025-9181 (uninitialized memory) were closed, which also presented security risks.
Why is this so dangerous?
The vulnerabilities identified are particularly threatening because they:
- Complete system compromise can enable
- Sandbox security mechanisms circumvent
- Both desktop and mobile devices affect
- No visible signs Leaving a successful attack
What Users Should Do Now
Immediate actions:
- Check updates: Open Firefox or Thunderbird and check whether you are using the latest version from the Help menu → About Firefox/Thunderbird
- Enable automatic updates: Make sure automatic updates are enabled
- Perform a restart: Restart the applications after the update
- Systems scan: Perform a full antivirus scan
Thunderbird users: Additional security
For Thunderbird users, there is a reassuring message: "These vulnerabilities usually cannot be exploited via emails in Thunderbird because scripting is disabled when reading emails", but they pose risks in browser-like contexts.
Current threat situation
No active attacks on these vulnerabilities have been reported so far. Mozilla also hasn't released any indicators that would help identify already compromised systems. This makes preventive updates all the more important.
Additional context: Phishing campaign
The latest security updates take place against the backdrop of a phishing campaign that Mozilla warned of in early August. Unknown attackers attempted to steal access data from add-on developers via fake emails. The scale and success of this campaign is not yet known.
conclusion
The latest security updates for Firefox and Thunderbird are critical and should be installed by all users immediately. The vulnerabilities identified could lead to serious security breaches if exploited successfully.
Users should not only install the updates, but also reconsider their general security practices: Regular updates, ideally automatically, as well as careful surfing behavior and the use of additional security software remain important building blocks for digital security as before.
Article 5
Customs raid at GamesCom exposes undeclared work
The largest computer game fair in the world became the scene of a large-scale customs raid on the opening day. With almost 60 emergency workers from the financial control of undeclared work, customs moved in and secured all access to the fair
After one Customs press release it was already ‘hot’ on the opening day at GamesCom’s trade fair grounds. Investigators reviewed nearly 150 employees from more than 40 security companies on the opening day. The results were alarming: About one third of the people checked showed evidence of undeclared work.
The violations in detail: In almost fifty cases, there were indications that those affected were not properly registered for social security by their employer. In addition, there are first indications of twelve cases of abuse of social benefits.
Particularly spicy: Numerous law enforcement officers said they were working the first day, including department heads with responsibility for numerous employees. The inspections took place not only at the entrances – also in the halls and on the open spaces, the officials checked, where also security personnel were deployed.
The case shows that systematic labour law violations can also occur at large-scale events – and customs consistently takes action against them.
Article 6
Critical Zero-Day Vulnerability in Apple Devices: CVE-2025-43300 already actively exploited
Apple has again released a critical security update to close a zero-day vulnerability that has already been exploited in targeted attacks.
The vulnerability, cataloged as CVE-2025-43300, affects iOS, iPadOS and macOS and poses a significant threat to millions of Apple users worldwide.
What is CVE-2025-43300?
CVE-2025-43300 is an out-of-bounds write vulnerability in Apple’s ImageIO framework with a CVSS score of 8.8, which it classifies as ‘highly critical’. The ImageIO framework is a central component used by apps to process and display image formats.
The technical details:
- Vulnerability type: Out-of-Bounds Write
- Affected component: ImageIO Framework
- CVSS score: 8.8 (high)
- Exploitation: Already active in targeted attacks
How does the attack work?
The vulnerability can be caused by processing a malicious image file. If an affected device processes a manipulated image file, this can lead to exploitable memory corruption.
Attack vectors:
- Malicious image files via email attachments
- Compromised websites with manipulated images
- Messaging apps and social media
- Any application that processes images automatically
The particularly dangerous: Exploitation can take place without the user actively clicking on the image file – automatic loading or processing is sufficient.
Affected systems and updates
Apple has confirmed that the vulnerability has already been exploited in ‘extremely sophisticated attacks’ against specific targets. Affected are:
iOS and iPadOS:
- iOS 18.6.2 and iPadOS 18.6.2 (latest versions)
- iPadOS 17.7.10 (older supported versions)
macOS:
- macOS Sequoia 15.6.1
- macOS Sonoma 14.7.8
- macOS Ventura 13.7.8
Apple fixed the vulnerability with improved Bounds-Checking mechanisms that prevent programs from writing outside of their assigned memory areas.
The Importance of Zero-Day Vulnerabilities
CVE-2025-43300 is already the seventh actively exploited zero-day vulnerability that Apple fixed this year. This accumulation shows several disturbing trends:
Rising threat situation:
- Cybercriminals Invest More in Zero-Day Exploits
- Apple devices are increasingly targeted
- The complexity and sophistication of attacks is constantly increasing
Out-of-Bounds-Write Attacks: This type of vulnerability is particularly dangerous because it allows attackers to write code to memory areas where the system executes it with elevated privileges. As a result, attackers can:
- Bypass system controls
- Installing malicious software with administrator privileges
- Access sensitive data
- Compromise the entire device
Immediate protective measures
1. Update immediately: All Apple users should immediately install the latest security updates. Updates are available through the system settings.
2. Enable automatic updates: Make sure automatic security updates are enabled to automatically receive future patches.
3. Beware of Unknown Images:
- Does not open images from dubious or untrustworthy sources
- Be careful with email attachments
- Checks suspicious links before clicking
4. Network security:
- Uses trusted WiFi networks
- Enables firewalls and other security features
- Monitors unusual device activity
Outlook and Conclusion
CVE-2025-43300 highlights the continued threat of zero-day vulnerabilities and the need for a proactive IT security strategy. The fact that the seventh zero-day vulnerability in Apple systems has already been actively exploited this year shows the worsening threat situation.
The days of sitting back as an Apple user and smiling about Windows or Android security flaws seem to be over.
Key findings:
- Zero-day attacks are becoming more frequent and sophisticated
- Automatic security updates are essential
- A multi-layered security strategy is essential
- User Awareness Plays a Crucial Role
Apple's quick response deserves recognition, but the accumulation of such vulnerabilities should prompt all Apple users to rethink and strengthen their security practices.
Recommendation for action:
Installs the security updates immediately and checks the general IT security measures. In today's threat landscape, prevention is key to protecting your digital assets and all personal data.
Article 7
Gamers wanted: The BND discovers Gamescom as a recruitment hotspot
The Federal Intelligence Service (BND) has a new strategy for finding young talent, which takes it straight to the heart of the gaming community – Gamescom.
What seems like an unexpected step at first glance makes sense on closer inspection. If you think of the BND, you probably have pictures of secret agents and espionage films in your head. But reality is much more shaped by state-of-the-art technology, digital communication and cybersecurity. This is where gamers come into play.
Why gamers?
The skills that many gamers acquire over time are highly relevant to the BND. Just think of:
- Quick comprehension and decision-making: In action-packed games, fractions of a second must decide on victory or defeat. This capability is worth it in the operating environment of the BND Gold.
- Problem-solving competence: Solving complex puzzles, finding vulnerabilities in systems or developing new strategies are everyday challenges for gamers.
- Endurance and Concentration: Focusing on a task for hours without losing focus is part of the everyday life of many players.
- Teamwork ability: In multiplayer games, effective collaboration is key to success.
The BND is looking for creative minds, Those who don't think in traditional patterns. People who are able to recognize patterns, decipher hidden information, and stay cool under pressure. For this, there was also an Develop your own game, that can currently be played at Gamescom at the BND stand.
From the controller to the keyboard of the BND
The strategy that Gamescom uses as a recruitment platform is a smart move. Instead of only being present at classic job fairs, the BND goes where it meets a target group with the talents it is looking for. It shows that it is modernizing and recognizing the potential of an often underestimated community. Unlike the BND, for example, the Bundeswehr has long recognized the trade fair as an opportunity and not only promotes new professionals, but also uses the fair in a targeted manner to present its own image as a ‘fit against threats, especially in cyberspace’. The Bundeswehr also needs gamers' skills in many areas, such as handling joysticks and controllers, responsiveness and multitasking.
This step underscores how important IT security has become for government institutions. With the increasing shortage of skilled workers in this sector, new avenues must be broken down. The BND has recognized that the next generation of cybersecurity experts, analysts and technicians is growing not only in lecture halls, but also in the digital worlds of computer games.
It remains exciting to see which talents the BND will discover at this year's Gamescom and whether this unconventional approach will bear fruit. However, one thing is certain: Gamescom is more than just a gaming fair – it is now also a place for next-generation secret agents.
Article 8
Intel is now partially nationalized: A deal with Trump
Intel becomes a state-owned company. The United States has 9.9 % the shares secured – in return, CEO Lip-Bu Tan is allowed to keep his position.
But what is really behind this deal, which was threaded by US President Donald Trump?
A Deal on the Abyss
The pact equates to a slingshot price for the United States. Instead of fresh capital, Trump is only freeing up subsidies that Intel says are ‘CHIPS and Science Act“ He was allowed to do so, but was blocked by his government. In addition, there are already disbursed subsidies.
Trump himself announced the deal: Tan, who had previously been pushed by Trump to resign, had given him the ten billion dollars for the United States in return for his job. On closer inspection, however, this is not the case.
The "CHIPS and Science Act" It was passed under President Joe Biden to strengthen U.S. semiconductor production and reduce reliance on Asian manufacturers. Although Trump is not a fan of this law, he is now using it to his advantage.
What the U.S. Gets (and Doesn't)
- The facts: The U.S. will receive the stock package at a significant discount price of $20.47 per share, which is 17 percent. % below the closing price of the previous week. Usually, large stock packages are sold with price premiums.
- The exchange: In return for the shares, the remaining $8.9 billion Subsidies granted to Intel from the ‘CHIPS Act’ entitled.
- Options for the future: Should Intel exceed 49 in the next five years? % If the company sells its Intel Foundry chips, the U.S. will be allowed a further five chips. % Buy the company at an even lower price of $20 per share.
A side issue of national security?
The deal raises questions about national security. The U.S. government renounces important clauses of the ‘CHIPS Act’, which actually serve to prevent abuse and ensure national security.
These safeguards include:
- Profit sharing: Beneficiaries of subsidies should repay part of their excess profits to the State.
- Infrastructure for employees: Companies should offer affordable kindergarten places.
- Use of funds: The grants may not be used for distributions to shareholders.
- Protection from competition: Beneficiaries may not build new factories in countries considered a threat (especially China) or significantly increase the capacity of factories there for 10 years.
These rules will no longer apply to Intel. At the same time, Trump's concerns about CEO Tan, especially his alleged ties to Chinese chip companies and the Communist Party of the People's Republic of China, suddenly seem to be completely forgotten.
Thus, the US government not only loses the opportunity to exert influence, but also gives the ‘CHIPS Act’ set security rules to complete the deal.
Article 9
Surprised Pikachu – German government is dependent on US Tech and not digitally sovereign as announced
A shocking realization shakes the republic: Germany is technologically dependent. Who would have thought that?
The federal government has an groundbreaking discovery The experts haven't been surprised for years: Germany is cautiously worded ‘depending on individual foreign suppliers in some areas of technology’. Cloud infrastructure, operating systems, network technology – all new territory, one could say.
No? Yes, of course! Ohhhh! The Great Awakening
The lead Digital Ministry concedes in a small voice what IT experts could have predicted as early as 2010: US companies such as Amazon, Google and Microsoft dominate the German market. Shocking to you! Who could have guessed that decades of inaction in digital politics would lead to dependencies?
The irony of everyday life
Particularly spicy: While the government publicly philosophises about ‘digital sovereignty’, its own ministries are diligently using AWS and Microsoft services. Even the federal police entrust their sensitive data to American clouds. It's like complaining about being overweight while eating the third doner of the day.
The Procurement Office has even recently concluded four new framework agreements with the hyperscalers. Motto: “Digital sovereignty? Yes, but only after the next Microsoft deal!” Way to go, yay!
The Cloud Act sends greetings
The fact that U.S. companies are required by the Cloud Act to release customer data to U.S. security agencies, without a court order, seems to the government to know, but not really disturb. The main thing is that the Excel spreadsheets run smoothly in the Azure cloud.
“Are you aware that German data has already been passed on? We don't," the government's honest response said. Sometimes ignorance is a blessing.
The Great Rescue
But don't worry! The federal government has a plan: OpenDesk as a Microsoft 365 alternative and OpenCode as a portal for open source software. It's like trying to stop the Titanic sinking with a single life jacket – but hey, at least you're trying.
Chancellor Friedrich Merz and Digital Minister Karsten Wildberger repeatedly emphasise the importance of ‘digital sovereignty’. It's almost touching how seriously they take this while presumably managing their appointments in Outlook.
IPCEI – Hope dies last
Major Tamtam announces "projects of common European interest" for edge computing and cloud infrastructures. IPCEI-ECI, IPCEI Cloud – Abbreviations to give hope. Whether this will be more than PowerPoint presentations will become clear.
Meanwhile, the Open Source Business Alliance and other stakeholders are calling for ‘high-pressure’ alternatives to be developed. By the way, they've been doing this for years. But better now with high pressure (demand) than never, right?
Conclusion: Better late than never?
The Federal Government’s finding is similar to the famous ‘Surprised Pikachu’ meme: One does nothing for digital sovereignty for years and is then amazed to be dependent. After all, one can say: Insight is the first step to improvement.
Whether real alternatives will emerge from the announced measures or only further declarations of intent will be revealed. Until then, we still have the image of a government that preaches digital independence while sitting in the American cloud.
In this sense: Surprise! ⁇
Let's close again this week with a quote from the wise ISO-27001 safety officer Sun-Tsu: ‘Choose your fights wisely” Not every warning or problem requires an immediate, elaborate response. Prioritize threats and focus on the ones that could do the most damage.