Today in the ‘classic style’: Throughout the week, we worked through technology blogs and IT news to put together nine contributions from week 11.8 – 17.8 (KW33-2025). So keep reading now, message 8 will shock you! Here is the "Wews of the Week":
Libarchive gap | WinRAR exploit | Digi ranking | AI application | DefCon Phishing | Geofencing backups | PrivateCloudOutlook | CyberResilienceAct | DigitalDetox
Article 1
Do you use libarchive? Then you should act now!
I want to talk today about a security flaw that has caused some excitement in recent weeks. It is about libarchive, An open source compression library that is used by many of us on a daily basis without our being aware of it.
A vulnerability that was initially classified as harmless turned out to be as a critical threat – and this has only become so well known in the last few days.
An initial misunderstanding
A few months ago, the gap was reported by a security researcher named Tobias Stöckmann. The developers of libarchive responded quickly and released a new version, 3.8.0, to fix the problem. Initially, Red Hat rated the vulnerability as having a CVSS of 3.9 and a ‘low’ risk. A value that most of us might not have immediately put on alert.
Then came the turnaround. The US National Institute of Standards and Technology (NIST) has taken a closer look at the matter and reassessed it. With an updated attack vector, they came to an alarming conclusion: The CVSS value is 9.8, What is the gap as critical graded.
What exactly is the problem?
The vulnerability under the identifier CVE-2025-5914 | EUVD-2025-17572 running, is in the function archive_read_format_rar_seek_data(). If you .rararchives, it can be processed there to a Integer overflow Come on, come on. What happens next is a so-called ‘double free’: Resources that have already been released will be released a second time.
This can have fatal consequences. Attackers could exploit this error to manipulate memory, execute malicious code, or cause a denial-of-service (DoS) state that paralyzes your system.
Who is affected?
You might be thinking now, ‘libarchive, that only applies to Linux systems, right?’ Wrong thinking. Admittedly set Many Linux and Unix distributions The library, but also Microsoft Windows is affected.
Since Microsoft Build 2023, Microsoft has been using the open source libarchive project to provide native support for various archive formats such as .tar, .rar and .7z to ensure. So it is very likely that your Windows system is also vulnerable. It is unclear whether Microsoft has already delivered the error-corrected library.
What should you do now?
The urgency of the situation is due to the Warning from the CERT-Bund (the German IT security authority) and the DFN underlined the reassessment of the gap by NIST.gov.
So if you are using a system that relies on libarchive, you should urgently check if there is an update. Whether you're using Linux, macOS, or Windows, check your system management or package manager and install the latest updates. It's better to play it safe and act proactively before it's too late.
Article 2
Be careful with WinRAR this week!
You are using WinRAR? Then you should be attentive now. A critical vulnerability has been discovered that is not only dangerous, but is also actively exploited by criminals. You should install the update immediately!
What happened?
Eset security researchers have found a vulnerability (CVE-2025-8088 | EUVD-2025-23983), which allows attackers to execute malicious code on your computer. How does it work?
The gap is a so-called ‘path traversal’ vulnerability. This means that an attacker can create a manipulated archive file. If you unpack it with a vulnerable version of WinRAR, the malicious code can run on your system. The risk is high (CVSS 8.4).
Particularly explosive: According to Eset, this gap is already being exploited. Cybercriminals send emails with prepared RAR files to install backdoors that can then be used to launch further attacks.
What do you have to do?
The good news: WinRAR has already reacted and the Version 7.13 published, which closes the gap. By the way, the Unix and Android versions are not affected, the older Windows versions already.
My advice to you: Go to the WinRAR download page and download the latest version. It's a small effort for your safety that's definitely worth it.
Alternatively, you can also use the Windows command winget search winrar search for the exact name in your installation and then use winget upgrade rarlab.winrar (the name to be inserted is the displayed ID) start the update.
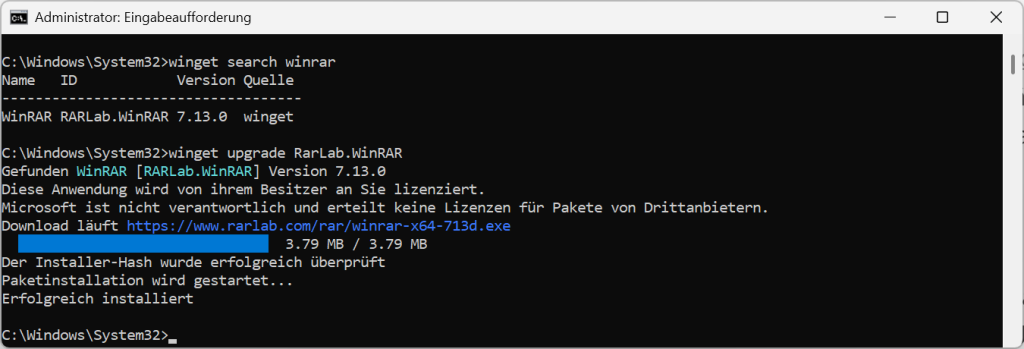
Alternatively, you can also update your entire system with winget, for which you then use the command in your admin CMD winget upgrade --all
Article 3
Germany ranks 14th out of 27 in digitalisation in the EU
The good news: It's going up! In the current Bitkom DESI index, Germany has climbed two places and is now ranked 14th out of 27 EU countries.
This is a slight improvement, but we are still in the middle of the ‘new country’. On silicon.de I have an article on this read. This is about the current DESI index of Bitkom Report on which the figures are based. The report is also as PDF.
What's going well?
- Economy: German companies are now quite fit, especially when it comes to future technologies such as artificial intelligence and cloud services. In this area, Germany is even in the top 10, albeit only in 8th place.
- Infrastructure: We are doing well in grid expansion. Almost all households have 4G/5G, and many can now even use gigabit ports.
Where else is there any catching up?
- Digital management: Unfortunately, we are still far behind here. In the ranking, we only make it to 21st place. The use of digital administrative services is significantly lower than the EU average, and many government services are simply still not digitally available.
- Digital skills: Here, too, there is air upwards. Only one in five Germans has above-average IT skills, which is below the EU average.
In summary, it can be said: We are probably slowly on the right track, but there is still a lot to do, especially in the areas of administration and skills, to become truly digitally sovereign.
Digitalisation is seen as a shared task that must be tackled jointly by politics, the economy and society.
Article 4
Companies are slowly returning to on-site interviews out of concerns about AI
Gradually, the job search shifts from the often pure online area back to face-to-face events with the aim of sorting out the Schummler.
You probably remember the times when online interviews were the new standard. No stress with the journey, no tightening and comfortable from your own desk. That was super convenient! But this trend seems to be taking a surprising turn.
Companies such as Google and Cisco return, As reported by Golem, back again to the old-fashioned, personal interview. The reason for this is something that may surprise some: fraud.
The convenience of virtual conversations has become a playground for clever (and dishonest) applicants who use AI and other tricks to fake skills.
The Fraud That Forces Businesses to Return
Imagine: You are applying for software development. In the online interview you get a programming task. But instead of coding yourself, let an AI do the job. Within seconds, she delivers the perfect code that will make you look like a ‘man or woman from the field’ in the interviewer’s eyes.
This is no longer science fiction, but reality. According to the Wall Street Journal The percentage of U.S. companies that demand a face-to-face meeting has risen from 5 percent. % in 2024 to a total of 30 % in 2025. This is a clear announcement.
But it's not just about AI. Some of the scoundrels become even more brazen. The Market researcher from Gartner They found that 6 % the applicant admits to having been represented in an interview by someone else. Counterfeit profiles give fraudsters access to sensitive company data or, in the most extreme cases, money. It sounds nasty enough, but Gartner predicts that by 2028, even one in four applicant profiles could be fake. It's hard, isn't it?
How High-Tech Cheat Works Exactly
Probably all of you have already used tools like ChatGPT. But how exactly are they used in online interviews? This is a simple but effective process:
- Listening (Voice2Text): Using special apps or browser extensions, the spoken word of your interviewer is recorded in real time and converted to text using speech recognition. This is a technology we know from Alexa or Siri.
- Thinking (LLM analysis): This text is immediately sent to a large language model (LLM) such as GPT, Gemini or similar. AI analyzes the question, understands the context, and looks for the best possible, most professional, and most persuasive answer.
- Answers (text output): The response generated by the AI will then appear on your screen in a flash. Sometimes it even appears in an unobtrusive window. The applicant only has to read the answer and reproduce it as naturally as possible.
A perfect workflow to hide a lack of expertise. And yes, there are already ready-made apps and tools that offer just that. You may not know any names, but Reports from Business Insider confirm that: such helpers such as that of Chungin ‘Roy’ Lee, who even He flew from his university. Probably flooding the market.
What does this mean for you now?
Returning to face-to-face conversation is not harassment, but a necessary response from companies. They want to make sure again that the person sitting in front of them really has the skills they claim to have. A personal conversation is hard to fake.
For you, this means: Get ready for the real handshake and eye contact again. Practice your answers, learn your code, and just be yourself. Even an honest ‘I don’t know that by heart, but I would google fast’ in response will certainly not leave you in a bad mood, because no one knows everything. At the end of the day, trust is the most important currency, and that's best built face-to-face.
So, grab some decent clothes and get ready to convince yourself in person again!
Article 5
Beware of phishing! Microsoft's login page as an attack surface
DefCon, one of the world's largest hacker conferences, is always the venue for exciting and sometimes disturbing discoveries.
This year worried Keanu Nys by Spotit from Belgium for sensation with a presentation that should remind us all of the importance of staying vigilant. I read about it at heise.de.
When the official login becomes a phishing tool
Nys, who is also the author of GraphSpy and lecturer on Azure Red Teaming Bootcamps, has taken the challenges of classic phishing attacks as a starting point for his research. Classic attacks often fail due to email security solutions or the awareness of users who pay attention to suspicious domains. His goal was to find out if he was trustworthy. login.microsoftonline.com This website can be misused for phishing purposes.
Spolier alarm. Here you can find his presentation as PDF.
The presentation showed that under certain circumstances, Microsoft's official login page, which we all know from services like Office 365, can be turned into a phishing platform. The core of the problem lies in the federation of domains, i.e. the domain association that facilitates the inconvenient, permanent password entry by SingleSignOn users. Nys has shown in his Def-Con presentation that attackers can easily adjust the federation configuration of a domain, e.g. micro-oft.com, redirect the login page to a fake login URL, which then retrieves the login credentials. With the help of its own font, which then displays an s from the hyphen for the presentation, the changed domain is not even noticeable.
Some of you may know that even from the ebay.com domain, which was provided with Cyrillic e also deceptively real as ‘official’ went through.
But even older phishing attempts via so-called lookalike domains (microsaft.com) or the long-popular typosquatting with the typical letter turner (mircosoft.com) were and are popular, but at least stand out on closer inspection.
MFA is not a 100% guarantee
Pass Through Authentication (PTA) allows attackers to verify that the captured credentials are valid and to obtain a session ID that allows them to use all of the tenant's services (M365, Storage, and more). Multi-factor authentication (MFA), which is often regarded as a rescuer in need, is also not insurmountable. Nys demonstrated that attackers can use a sophisticated method to anticipate MFA queries and thus overcome this hurdle. This requires two accounts, but it shows that even supposedly secure systems have vulnerabilities.
What this means for users
The frightening thing about this method: Since the attacks then come from an official Microsoft domain with correct login data, they cannot be stopped by traditional security measures such as firewalls or DNS filters. The only way to protect yourself at the moment is to educate about such methods of theft and in the vigilance of users. It is crucial that we learn to pay attention to even the smallest details and, in case of doubt, to be too much rather than too little suspicious.
The presentation at Def Con 33 is a clear signal to Microsoft to review its security protocols and make fewer compromises in favor of features. Until then, users have no choice but to keep their eyes open and pay attention to our digital security.
What this means for admins
Detailed information and recommendations for action
The Evolution of Phishing Attacks & Traditional Phishing Challenges
Traditional phishing attacks face several fundamental problems:
- Infrastructure construction: Attackers must deploy their own servers, domains and SSL certificates
- credibility: Fake login pages must look convincing
- detection: Security tools are increasingly detecting suspicious domains and URLs
- maintenance: Phishing infrastructure is quickly detected and blocked
The Microsoft advantage
The techniques presented by Nys elegantly circumvent these problems by using the trusted Microsoft infrastructure itself:
- trust: Attacks are carried out directly via
login.microsoftonline.com - credibility: No fake pages required
- bypass: Security tools implicitly trust Microsoft domains
- persistence: Hard to block because based on legitimate functionality
Device code phishing: The basis
What is Device Code Authentication?
Device Code Authentication is an OAuth 2.0 flow developed by Microsoft, originally designed for input-restricted devices such as smart TVs or IoT devices. The process works as follows:
- Generation of code: A device requests a device code from Microsoft
- User interaction: The user visits
microsoft.com/deviceloginon another device - Code input: The 9-digit user code is entered
- authentication: The user logs in with his credentials
- Receipt of tokens: The original device gets access and refresh tokens
Abuse for phishing
Attackers can abuse this legitimate mechanism for phishing attacks:
1. Attacker generates device code for Microsoft Graph API 2. Phishing email with link to microsoft.com/devicelogin will be sent 3. Victim enters the code and authenticates 4. Attacker gains full access to user accountExample of a phishing email:
Here is the link to the important document: https://microsoft.com/devicelogin Use the following code: ABC123DEF Sincerely, IT DepartmentPsychological factors
The effectiveness of these attacks is based on several psychological principles:
- authority: Microsoft URLs suggest trustworthiness
- familiarity: Users are used to Microsoft login processes
- Time pressure: 15-minute limit creates pressure to act
- Social engineering: Skillfully selected pretexts (team meetings, important documents)
Advanced techniques: Beyond Device Code Flow
Client ID manipulation
By selecting specific client IDs, attackers can manipulate the displayed app names:
- Microsoft Teams:
1fec8e78-bce4-4aaf-ab1b-5451cc387264 - Microsoft Office:
d3590ed6-52b3-4102-aeff-aad2292ab01c - SharePoint: Different IDs depending on the desired pretext
The warning "You sign in to Microsoft Teams" is less suspicious than generic messages.
FOCI (Family of Client IDs) usage
Microsoft implements FOCI, which allows certain refresh tokens to be used for multiple applications:
# Example: Token refresh for various services in the PowerShell $refreshToken = "0.AAAAxkwD..." # Exchange Online Access Get-AccessToken -RefreshToken $refreshToken -Resource "https://outlook.office365.com" # SharePoint Access Get-AccessToken -RefreshToken $refreshToken -Resource "https://graph.microsoft.com" # Azure management access Get-AccessToken -RefreshToken $refreshToken -Resource "https://management.azure.com"Geolocation spoofing
Attackers can bypass location warnings:
- Use of VPNs or cloud instances in the target country
- Reduces suspicion of ‘You are registering from Germany’ notifications
- Significantly increases the probability of success
Practical implementation with GraphSpy
Tool overview
GraphSpy, developed by Keanu Nys, automates many of the techniques described:
- Multi-threading: Simultaneous polling of multiple device codes
- Token management: Automatic storage and management of tokens
- Post-exploitation: Integrated enumeration and lateral movement tools
Example scenario
# Generate device code graphspy --generate-device-code --client-id "Microsoft Teams" --resource "https://graph.microsoft.com" # Code: XYZ789ABC
# URL: https://microsoft.com/devicelogin
# Prepare phishing email send-phishing-mail --recipient "target@company.com" \ --subject "Urgent Teams Meeting" \ --code "XYZ789ABC" # Start automatic polling graphspy --poll-codes --interval 5Successful compromise
After successful authentication, the following options are available:
- Email access: Read, send, forward emails
- SharePoint/OneDrive: Document access and manipulation
- teams: Send messages, join meetings
- Azure resources: Depending on permission Management access
Advanced Adversary-in-the-Middle (AiTM) bypass
Traditional AiTM recognition
Modern security solutions detect AiTM attacks by:
- TLS Fingerprinting: Analysis of SSL/TLS handshake parameters
- Certificate anomalies: Detection of self-signed or suspicious certificates
- Behavior analysis: Unusual login patterns
Circumvention strategies
The presented techniques bypass AiTM detections by:
- Legitimate infrastructure: No proxy or MiTM required
- Original certificates: Use of real Microsoft SSL certificates
- Normal traffic patterns: Authentication follows legitimate OAuth flows
Detection and defence
Detection strategies
1. Anomaly detection in logs
-- Suspicious device code flows in SQL SELECT user_id, client_name, ip_address, country, timestamp FROM signin_logs WHERE client_name = 'Microsoft Office' AND ip_country != user_home_country AND timestamp > NOW() - INTERVAL 1 DAY ORDER BY timestamp DESC;2. Geolocation monitoring
- Monitoring of notifications from unusual countries
- Correlation of device code logins with known user locations
- Automatic alerts for geographical anomalies
3. Client pattern analysis
# PowerShell script for anomaly detection
$suspiciousClients = @('Microsoft Office', 'Microsoft Teams') $recentLogins = Get-AzureADAuditSignInLogs -Filter "createdDateTime gt $((Get-Date).AddDays(-1))" $suspiciousLogins = $recentLogins Where Where-Object { $_.AppDisplayName -in $suspiciousClients -and $_.IpAddress -notin $trustedIPRanges }Prevention measures
1. Conditional access policies
{ "displayName": "Block Device Code from Untrusted Locations", "state": "enabled", "conditions": { "applications": { "includeApplications": ["All"] }, "locations": { "excludeLocations": ["trusted-locations"] }, "clientAppTypes": ["deviceCodeAuthZ"] }, "grantControls": { "operator": "OR", "builtInControls": ["block"] } }2. Application restrictions
- Disabling Device Code Flow for Unneeded Applications
- Whitelist-based Client ID control
- Regular review of registered applications
3. User training
Training content should include:
- reconnaissance Device Code Phishing
- Warning signals Recognize (unexpected login codes)
- verification Login requests via alternative channels
- Incident response Suspected compromise
Incident Response and Remediation
Immediate measures in case of suspicion
- Token invalidation:
# Revoke all Refresh tokens of a user Revoke-AzureADUserAllRefreshToken -ObjectId $userId- Password reset (also invalidates all tokens)
- End of session in all applications
- Forensic analysis the Registration Logs
Long-term hardening
Multi-factor authentication
- Adaptive MFA: Risk-based authentication
- FIDO2/WebAuthn: Hardware-based tokens
- APP-based MFA: Microsoft Authenticator with Number Matching
Zero trust architecture
⁇ ─────────────────── ⁇ ⁇ ──────────────── ⁇ ⁇ ────────── ⁇ ⁇ Device Trust ◄ Identity Identity Trust ◄ ◄ Apply ◄ Compliance ⁇ ──── ⁇ Verification ⁇ ───── ⁇ Authorization ⁇ ⁇ ───────────────── ⁇ ⁇ ──────── ⁇ ⁇ ───────────── ⁇ ⁇ ───────────Technical deep dive: OAuth Flow Manipulation
Standard OAuth 2.0 Device Flow
sequenceDiagram participant D as Device participant AS as Auth Server participant U as User participant UB as User Browser D->>AS: POST /devicecode AS->>D: device_code, user_code, verification_uri D->>U: Display user_code + verification_uri U->>UB: Navigate to verification_uri UB->>AS: Enter user_code AS->>UB: Authentication prompt UB->>AS: Credentials + consent loop Polling D->>AS: POST /token (device_code) AS->>D: authorization_pending / access_token endManipulated Flow for Phishing
sequenceDiagram participant A as Attacker participant AS as Auth Server participant V as Victim participant VB as Victim Browser A->AS: POST /devicecode AS->>A: device_code, user_code, verification_uri A->>V: Phishing email (user_code + verification_uri) V->>VB: Navigate to verification_uri VB->>AS: Enter user_code AS->>VB: "Sign in to Microsoft Teams" VB->>AS: Victim credentials loop Attacker Polling A->>AS: POST /token (device_code) AS->>A: access_token, refresh_token endImpact on the cybersecurity landscape
Paradigm shift
The techniques presented represent a fundamental change:
- From infrastructure-based to service-based: No need for your own phishing infrastructure
- From Imitation to Legitimation: Use of real Microsoft services
- From Detection to Prevention: Focus must be shifted to prevention
Implications for companies
Short/medium term:
- verification the Conditional Access Policies
- training Employees on new threats
- monitoring the Device Code Usage
In the long term:
- Zero trust-accelerate migration
- PasswordlessImplement strategies
- Threat intelligence Expand to OAuth attacks
Regulatory aspects
- GDPR: Incidents must be reported within 72 hours
- NIS2: Increased Cybersecurity Requirements in Critical Sectors
- compliance: Evidence of adequate security measures required
Future outlook and trends
Expected developments
- Tool sophistication: Further automation and integration into frameworks
- Scale increase: Mass phishing with device codes
- Evasion techniques: Bypassing Machine Learning-based Detection
Microsoft's response
Microsoft is expected to take the following actions:
- Enhanced warnings: Clearer alerts for device code flows
- Risk assessment: Smarter risk assessment based on context
- Policy controls: More granular administrative controls
Industry-wide implications
The techniques are also likely to be transferred to other identity providers:
- Google OAuth: Similar attack vectors could be possible
- SAML Provider: Corresponding flows could be abused
- OpenID Connect: Standardized protocols as attack surface
Practical recommendations
For security teams
- Immediate action:
- Device code policy review
- Conditional access audit
- User training update
- Medium-term projects:
- SIEM Rule Development
- Threat intelligence integration
- Incident Response Playbook Update
- Strategic initiatives:
- Zero Trust roadmap
- Passwordless migration
- Security culture program
For IT administrators
# Example: Conditional Access Policy for Device Code Blocking
$policy = New-Object Microsoft.Open.MSGraph.Model.ConditionalAccessPolicy $policy.DisplayName = "Block Untrusted Device Code Authentication" $policy.State = "Enabled" $conditions = New-Object Microsoft.Open.MSGraph.Model.ConditionalAccessConditionSet $conditions.Applications = @{IncludeApplications = @("All")} $conditions.ClientAppTypes = @("DeviceCodeAuth") $grantControls = New-Object Microsoft.Open.MSGraph.Model.ConditionalAccessGrantControls $grantControls.Operator = "OR" $grantControls.BuiltInControls = @("Block") $policy.Conditions = $conditions $policy.GrantControls = $grantControls New-MgIdentityConditionalAccessPolicy -BodyParameter $policyFor end users
Checklist for suspicious authentication requests:
- ✓ Did you expect to sign up for a new device?
- ✓ Do you recognize the location in the warning message?
- ✓ Has the request come through a trusted channel?
- ✓ Did you initiate the action yourself?
conclusion
The techniques presented at DefCon 33 mark a turning point in the evolution of phishing attacks. By cleverly exploiting legitimate Microsoft functionalities, attackers can bypass most traditional defenses and take advantage of the inherent trust in Microsoft services.
Key findings:
- Trust is a Vulnerability: The Trustworthiness of Microsoft Domains Becomes a Weapon
- Prevention of Detection: Since attacks are difficult to detect, prevention must be paramount
- A holistic approach is needed: Technical measures must be complemented by training
- Continuous evolution: Attackers adapt quickly, defense must keep up
The cybersecurity community faces the challenge of rethinking proven security models and developing new defense strategies. While Microsoft and other vendors are working on solutions, it's up to companies and security teams to proactively adjust their defenses.
The message is clear: In a world where even the most trusted domains can become an attack surface, a zero trust approach is no longer optional, but essential for modern cybersecurity.
Disclaimer: This article is based on the work of Keanu ‘RedByte’ Nys and the findings presented at DefCon 33 2025. All technical details are for reconnaissance and defence purposes only.
date: August 2025
sources: DefCon 33, GraphSpy Documentation + Github Wiki, MDSec Research, heise.de
Article 6
New offers for data/backup with European geofencing
You probably all know the French hosters OVHCloud or Scaleway, Exoscale from Switzerland or Aruba from Italy. They have their focus on data sovereignty in Europe, now we have one more special for backups.
Have you been thinking over the last few months about your data backups that are not only secure, but also securely hosted completely European? I'm here for one News on it-business.de, Which I have to share with you!
The two companies Impossible cloud and NAKIVO They have joined forces to launch a backup solution for Europe. And the best thing about it? They have deliberately opted for an infrastructure that only runs on our continent. This is a welcome statement with NIS2, DORA, SOC2 or even the GDPR – always with the Damocles sword US-Cloud-Act In the back of your mind!
Why is this such a big deal?
Quite simply: It is about digital sovereignty. The new solution is not subject to the U.S. Cloud Act or other U.S. regulations. Your data is therefore guaranteed to remain in Europe and protected. This not only makes for a good feeling, especially if you keep an eye on the increasingly strict data protection regulations, but also for real autonomy. For this purpose: Impossible Cloud also a nice blog post which summarizes the most important points well.
The solution is especially designed for MSPs (managed service providers) and resellers who want to offer their customers a secure and cost-effective backup solution. And here, too, there are some cool advantages:
- No hidden costs: No more unpredictable expenses. The solution has no Egress or API fees. This makes the costs predictable.
- Data protection according to GDPR: All data is stored in ISO-certified data centers in the EU and is GDPR compliant.
- Safe against ransomware: With features like Object Lock, your backups become unchangeable. This way you are optimally protected against ransomware attacks.
- Easy to use: Full S3 API compatibility makes it quick and easy to set up and integrate with existing environments.
In my opinion, this is a great step for anyone who values data security, cost control and compliance. The partnership between Impossible Cloud and NAKIVO shows that there are strong, sovereign alternatives to the major US providers.
Are you still looking for a European backup solution? Maybe it's worth a look.
Article 7
Broadcom's Private Cloud Outlook for 2025 shows rethinking in the IT industry
In particular, the private cloud benefits from better cost prediction capabilities, easier compliance with GenAI application requirements, and sensitivity to security and compliance rules.
Have you ever wondered what the future of the cloud looks like? A recent study by Broadcom, which „Private cloud Outlook 2025„, provides exciting insights and speaks of a real Cloud reset.
It seems like companies are fundamentally reevaluating their cloud strategies. Away from a pure public cloud focus to a conscious mix in which the private cloud plays a central role again.
Private cloud on the rise: The facts speak for themselves
The study, which surveyed 1,800 senior IT decision makers worldwide, It shows a clear trend:
- A mix of public and private cloud is the norm: Set today 92 % companies on a mix of private and public clouds. Only 15 % prefer a pure public cloud model, and only 10 % They only want a private cloud.
- Private cloud as a strategic priority: More than half of respondents (53 %) indicates that building new workloads in a private cloud is a top priority over the next three years.
- Retrieval of workloads: A third of companies have already moved workloads from the public cloud to the private cloud, and 69 % Consider this step. The main reasons for this are security and compliance concerns.
- Modern instead of outdated: The image of the private cloud as a solution only for legacy applications is a thing of the past. 84 % Today, companies use them for both traditional and modern, cloud-native applications.
The driving forces behind change
Why this change? The study identifies three main factors driving cloud reset:
1. Security, data protection and compliance
In a world where data is becoming more valuable and regulations are becoming more stringent, security and compliance are coming to the fore.
- High level of trust: 92 % Respondents trust their private cloud when it comes to security and compliance requirements.
- Concerns in the public cloud: 66 % respondents are ‘very’ or ‘extremely’ concerned when storing data in public cloud environments.
- Top reason for the relocation: Security risks are the most important reason for relocating workloads. When it comes to public cloud use, there are 29 security risks. % The biggest challenge.
2. Cost control and financial transparency
The public cloud can quickly become confusing and expensive. The private cloud scores here with its predictability.
- Waste in the public cloud: 94 % Companies believe that some of their public cloud spending is being wasted. Nearly half (49) %This waste is estimated to be over 25 years old. % of total expenditure.
- Financial transparency: 90 % IT decision makers appreciate the financial transparency and predictability of private clouds.
3. Generative AI
Generative AI applications present companies with new challenges, especially in terms of data protection.
- Data protection as the main problem: Data Protection and Security Concerns at 49 % the biggest obstacle to the introduction of GenAI.
- Equivalent use: Companies use private and public clouds almost equally for their GenAI workloads. 55 % Public Cloud and 56 % the private cloud for the execution of GenAI.
Challenges on the way to the private cloud
Despite the many benefits, there are two key hurdles businesses need to overcome to unlock the full potential of the private cloud..
- Silo structures: 33 % Organizations see isolated IT teams as the biggest challenge for the adoption of the private cloud. The good news: 81 % The companies are already restructuring their IT teams towards platform teams in order to break down these silos.
- Skills gap: 30 % Respondents cited a lack of internal skills and expertise as an obstacle. In fact, 80 % companies rely on professional services for cloud-related requirements.
My conclusion
This emerging Cloud reset This does not mean the end of the public cloud, but rather a conscious rethinking. It's about leveraging the strengths of each cloud environment and placing workloads where they're best off.
The private cloud provides the much-needed control, security and cost predictability that is becoming increasingly important in the era of GenAI and strict compliance requirements. The future is hybrid, and the private cloud has reclaimed a firm place at the heart of IT strategy.
Article 8
Reflections on the upcoming EU Cyber Resilience Act (CRA) +GPSR
The article, written by Rolf Schulz, deals with the decisive changes that the Cyber Resilience Act (CRA) and the General Product Safety Regulation (GPSR) for manufacturers of connected products.
The article on security-insider.de points out that two new sets of rules are fundamentally changing the rules of the game for the EU market:
- The Cyber Resilience Act (CRA): Officially referred to as Regulation (EU) 2024/2847, the CRA makes cybersecurity mandatory. The CRA has been in place since 11. December 2024, the transitional period for current stock runs until 12. December 2027. All new products and services must then be compliant. This is the big change: What used to be known as ‘nice-to-have’ is now a mandatory requirement for the CE marking. This rule applies to almost any product with digital elements that can be connected to a network, from routers to office apps.
- The General product safety regulation (GPSR): This Regulation has already entered into force on 13. December 2024 in force and updates the basic safety requirements for all products. It complements the CRA and ensures that both physical and digital risks are taken into account throughout the product lifecycle. However, for digital products where the CRA has stricter or equivalent rules, the CRA takes precedence.
Together, these two regulations form a new, mandatory regime: Without a sufficient level of cyber resilience, there is no CE mark, and without the CE mark, you will not have access to the European single market. An overly clear announcement.
What this means for you: Duties and deadlines
The article breaks down exactly what obligations you have as a manufacturer and what important dates you have to keep in mind.
Duties along the life cycle:
- You have to follow the principles of your products from the very beginning. Secure by design and by default develop.
- You are required to create a risk-oriented technical documentation, which also includes a software bill of materials (SBOM) and test protocols. This documentation shall: 10 years are kept.
- You must enclose an operating manual that allows a safe configuration.
- Once the product has been launched, you are required to Active vulnerability management to operate and provide security updates for as long as the product is expected to be in use.
The most important deadlines you should remember:
- The Reporting obligation under Article 14 CRA Already starting on 11 September 2026. This means that you will need to report an actively exploited vulnerability within 24 hours from this date.
- Market surveillance begins on 11 June 2026.
- This Regulation shall apply in full from: 11. December 2027.
- Products that are up to 11. December 2027 have been placed on the market, will continue to be considered compliant as long as they are not substantially altered.
Video and Critical Perspective
The article also includes a reference to a video titled ‘Critical questions on the CRA’, It's not just about what the article is about. In this video, as the title promises, the challenges of the new regulations are highlighted. Since it not only presents the facts, but also triggers an examination of the potential problems, such as the increased costs for manufacturers and the risk that innovations could migrate from the EU, I can only recommend it to you. It's best to see for yourself:
By the way, the author Rolf Schulz also has other interesting videos on the GNSEC Academy YouTube Channel It's worth stopping by!
Article 9
The word for Sunday: Digital Detox in the Classroom
Hey dear ones, do you also feel that our heads sometimes almost explode with all the digital impressions? We surf, scroll and swipe through life from an early age.
Gradually, something really exciting happens that should make us all think: Our neighbors in the north, Sweden and Denmark, are radically putting the brakes on the digitization of their schools.
Back to the roots: Chalk, chalkboard and paper
Yes, you read correctly. Instead of tablets and online tools, there are a kind of ‘digital detox’ in the classroom. The two countries are serious: Sweden invested more than 100 million euros in 2024 to re-purchase printed textbooks. The Swedish Minister of Education Lotta Edholm clearly explains this with scientific findings. She says analog learning environments are simply better at developing basic reading and writing skills.
They will also Mobile phones in class This decision is no longer accepted, but virtually all other countries in the EU also contribute to this decision through the bank.
Denmark's Minister of Education Mattias Tesfaye goes even further. He has publicly apologized for turning the students into ‘guinea pigs in a digital experiment’. That's sitting!
Why this educational turnaround? The facts are clear
The U-turn is anything but an abdominal decision. It is based on studies that provide alarming results. For example, in 2023, the Swedish Karolinska Institute published a study showing that students who read on-screen are on average two years behind those who learn from printed books. Science speaks a very clear language.
In Germany, too, the whole thing is observed with argus eyes. The National Academy of Sciences Leopoldina recommends, for example, a social media ban for children under 13 and a smartphone ban in schools up to the tenth grade. This shows that the topic is also at the top of the agenda in this country. And a survey by Yougov in mid-2025 showed that a large majority of us, namely over 90 percent of Germans, are in favour of restricting mobile phone use in schools.
Not without criticism
Of course, there are also votes against. Media scientist Ingrid Forsler described the complete return to analogue media as ‘populist’ and ‘short-sighted’. She stressed that technology in itself is neither the problem nor the solution, but dealing with it is crucial. The devices themselves are not evil, but our way of using them could be.
What do you think? Is returning to pen and paper the right way? Or should we rather learn to use digital tools better and more specifically?
Let's end this week again with a wisdom from our esteemed colleague Sun-Tsu from the Blue team:
Deception is a tool, even in IT security! Use honeypots and other deceptions to confuse attackers for as long as possible, uncover their intentions, and waste their resources.