Here for you nine interesting contributions from week 30.6 – 6.7 (KW27-2025) put together and summarised, two of which looked at in detail and provided with more details – almost once across my ‘wews’ world.
sudo chwoot | The Xbox 9000 | USB-C++ | 80k BTC | High-tech Doro | Citrix Bleed 2 | MF Resurrection | Nvidia $4B | Cisco ssh CUCM
Article 1
Critical sudo gap in many Linux distributions
The topic that overshadowed the whole week was probably the CVE-2025-32463 | EUVD-2025-19673 which, in principle, each unprivilegedn User root rights per sudo enabled.
exploit chwoot Already in circulation
The key points are:
The danger: A critical vulnerability in sudo (CVSS 9.3) allows local users to gain root privileges through an error in the chroot function. A working exploit code called ‘chwoot’ is publicly available and has been successfully tested on Ubuntu 24.04 and Fedora 41. Further details can be found, for example, at the boys of Golem.de:
Critical Vulnerability CVE-2025-32463 in sudo Endangers Linux Systems
Systems concerned: The Sudo versions 1.9.14 until 1.9.17 They are definitely affected, which puts millions of Linux systems at risk. Sources: borncity ⁇ heise. Debian 11 and 12 are not This is because they use older versions of Sudo.
solution: The vulnerability was fixed in sudo 1.9.17p1 of 28 June 2025. Most distributions have already provided security updates.
urgency: As a public exploit is available and exploitation is easy, administrators should immediately install the available updates, especially for multi-user systems and cloud environments.
Let's go into more detail:
overview
A Critical Vulnerability in the Widespread Linux Tool sudo It threatens millions of Linux systems worldwide. The vulnerability, known as CVE-2025-32463, allows unprivileged users to gain root privileges with minimal effort and thus take full control of the system.
Technical details
The vulnerability
- CVE ID: CVE-2025-32463
- CVSS score: 9.2 (critical)
- Affected component: chroot function in sudo
- exploitation: Local privilege escalation
Operation of the attack
The error lies in the implementation of the chroot function of sudo. Between two function calls, it calls the ‘Name Service Switch’ (NSS), which stores the file /etc/nsswitch.conf loading. An attacker can cause this feature to load a manipulated file with C code (a dynamic .so library) and execute it with root privileges.
The researchers called the exploit code ‘chwoot’ – a pun of words consisting of ‘chroot’ and ‘root’ that reflects the nature of the vulnerability.
Systems concerned
Sudo versions
- Definitely affected: Sudo versions 1.9.14 to 1.9.17
- Not affected: Versions before 1.8.32 (erroneous code was only introduced in 1.8.32)
- Unclear: Versions between 1.8.32 and 1.9.14 (not fully tested)
Linux distributions
Confirmed affected systems:
- Ubuntu 24.04.2 (Noble Numbat)
- Ubuntu 24.10 (Oracular Oriole)
- Ubuntu 25.04 (Plucky Puffin)
- Ubuntu LTS versions: 22.04 (Jammy), 20.04 (Focal), 18.04 (Bionic), 16.04 (Xenial), 14.04 (Trusty)
- Fedora 41
- openSUSE Tumbleweed (before snapshot of 02.07.2025)
Unaffected systems:
- Debian 11 (Bullseye) – uses sudo 1.9.5
- Debian 12 (Bookworm) – uses sudo 1.9.13
Discovery and publication
The weakness was caused by Rich Mirch of the ‘Stratascale Cyber Research Unit“ discovered and publicly documented on 30 June 2025.
Proof of Concept
A working exploit code is publicly available and has been successfully tested on various systems. The attack requires only a C compiler and is exploitable in the standard configuration of sudo.
Fixes and updates
Official solution
- Patched version: sudo 1.9.17p1 (available since 28 June 2025)
- solution: The problematic changes from version 1.9.14 have been undone
- future: The chroot function will be completely removed in future sudo versions
Distribution-specific updates
Ubuntu:
- All affected versions have received security updates
- Advisory: USN-7604-1
- Updates port the bugfix to the sudo version used
Debian:
- Bookworm: sudo 1.9.13p3-1+deb12u2 (patched as a precaution)
- Bullseye: sudo 1.9.5p2-3+deb11u2 (patched as a precaution)
openSUSE:
- Tumbleweed: sudo 1.9.17p1 from snapshot of 02.07.2025
Possibly also interesting:
Second vulnerability: CVE-2025-32462
At the same time, another sudo vulnerability was discovered:
detail
- CVE ID: CVE-2025-32462
- CVSS score: 2.8 (low priority)
- problem: Bypass host restrictions in sudoers configuration
- prerequisite: Special configuration in
/etc/sudoersrequired - Hidden since: 12 years in sudo
exploitation
This gap can only be exploited if:
- The attacker has access to a local account
- The sudoers file contains rules for other systems (remote hosts)
Risk assessment
High risk
- Easy to use: Low attack complexity
- Wide distribution: Affects millions of Linux systems
- Full compromise: Root rights = complete system control
- Public exploit: Functional code available
restrictions
- Local access required: Attackers must already have an account on the system
- Standard configuration: Works with standard sudo configuration
Recommended actions
Immediate steps
- Install updates: Priority is given to all available sudo updates
- Checking systems: Identify affected sudo version (
sudo --version) - Update cloud templates: Update VM Templates
- Strengthen monitoring: Monitor unusual sudo activities
Long-term measures
- Regular updates: Implement automated update processes
- Access control: Minimize and monitor local user accounts
- monitoring: Check logs for suspicious privilege escalations
workarounds
For CVE-2025-32462, Red Hat recommends as an interim solution:
- Removal of remote host rules from sudoers files
- Limitation to local account definitions
conclusion
This critical vulnerability highlights the importance of timely security updates in Linux environments. The combination of widespread adoption, ease of use, and available exploit code makes this vulnerability one of the most significant Linux vulnerabilities of 2025. System administrators should act immediately and apply the available updates.
Article 2
Microsoft kicks out 'over 9000' man at XBox
Although the reference is cute, the occasion is unfortunately more to howl. loud Bloomberg and SeattleTimes Tabula Rasa is currently being made in Microsoft's gaming division.
Microsoft continues massive wave of layoffs from 2023 and 2024
Microsoft has once again laid off thousands of employees at the beginning of its new fiscal year, continuing one of the largest series of layoffs in the company's history. Up to 4% of the workforce, just over 9,000 employees, could be affected by the current cuts. In Washington State alone, 830 workers lost their jobs.
Redundancies in a larger context
These layoffs follow two previous waves in May and June in which Microsoft has already laid off over 6,000 employees. Since May, the company has cut more than 15,000 jobs worldwide, including more than 3,100 in Washington. Microsoft emphasizes that the cuts are not performance-related and aim to reduce management levels and increase agility.
Areas concerned
Particularly affected are various divisions of the company, including sales, marketing and gaming. Gaming boss Phil Spencer confirmed cuts in his field, although the gaming division is running successfully. According to the Bloomberg article, the current wave of dismissals mainly affects employees from gaming, especially after the Record takeover Activision-Blizzard-King is also likely to affect some in Europe.
Sidenote: For the former colleagues who survived the clear-cut in Cork and are now potentially affected, the old Blizzard 600 group from 2012 is still available as a network for you!
AI investments as cost drivers
While Microsoft is cutting staff, the company is investing heavily in artificial intelligence. For the current fiscal year, Microsoft plans to spend more than $80 billion on infrastructure, an increase of $25 billion compared to the previous year. The high AI costs force the company to save elsewhere.
Paradoxical situation
Notably, these layoffs come after one of the best quarters in the company's history, with nearly $26 billion in profit at $70 billion in revenue. Experts see this as a continuation of the tech industry’s ‘rightsizing’ movement following the pandemic-related growth.
Article 3
FAQ/Articles about the many standards of USB-C
heise.de Helps you look:
Not every USB-C cable allows all functions!
The most important findings from this Heise articles reads as follows: Just because USB-C is on it and the plug fits does not mean that all functions are possible. As so often, it is only possible if you take the time and take a closer look.
Main problem: Diversity despite standardization
USB-C should be standardized, but the reality is different. There are still many different USB-C cables with different functions and qualities.
Reason for the differences: Cost optimization
Functional limitations: The result is cables with limited functionality
Price pressure: Consumers often buy the cheapest cable available
Manufacturer reaction: Companies reduce manufacturing costs by eliminating veins
The colleagues of ct3003 also have a Beautiful video and article with a lot more background at the start, have fun with Keno and Christoph:
Also there will be the quintessence, if there is no indication on the cable, only helps to try out what it actually can.
As a rule of thumb: Shorter cables up to a maximum of 1m tend to be faster or can transmit more watts, simply because longer cables are slowed down by physics. Good luck.
conclusion: When buying USB-C cables, you should not only look at the price, but better take into account the desired functionality first – depending on the required purpose (only charging vs. fast data transfer).
Article 4
80k Bitcoin on Independence Day ‘on the move’
The network has been discussing a rather spectacular transaction of no less than 80,000 Bitcoin since Friday, which has not been moved since 2011.
About Twitter – erm X of course – there is some insight into the transaction, including that the 80000 coins were split into 8 different addresses at 10000 each. Spectacular $8.6 billion represents the transaction at a Bitcoin unit price of 107,774 on 4.7 – YAY!
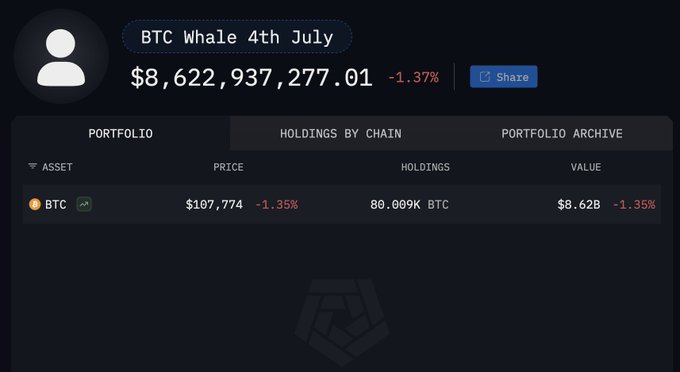
There was probably no test transfer of a small subset in advance (courageous or sure of victory?) and that due to the age of the coins probably someone only had to pay relatively small hand money for it.
It is also discussed diligently how much patience you have to show not to sell even at 1000 or 20000 prices and then look at years of lulls.
Whoever wants to stay on it is best to follow the Account, At least regular updates have been promised!
Article 5
High-tech agenda promotes key technologies
High-tech Agenda Germany – Key points Presented by Research Minister Doro Bär!
Objective: The initiative aims to strengthen Germany's competitiveness, security and sovereignty through research and technology. The focus is on new technologies to improve the lives of citizens, create prosperity and reduce dependencies.
Lead and timing: The Federal Ministry of Research, Technology and Space is leading the offensive, which starts this summer. The motto is: Competitiveness, value creation and sovereignty ‘made in Germany’.
Budget: The federal government wants to invest 5.5 billion euros, primarily in high-tech.
The six key technologies:
- Artificial intelligence
- Quantum technologies
- Microelectronics
- biotechnology
- Fusion and climate-neutral energy production
- Technologies for climate-neutral mobility
Starting point: Germany already has a strong base in all these areas with an internationally attractive science and research system, high technological performance and innovative companies.
The agenda aims to expand these existing strengths in a targeted manner and to position Germany as a leading technology location.
Implementation strategy and timetable:
Specific measures:
- Flagship initiatives for each of the six key technologies with clear timelines that agenda paper is already at the other ministries.
- First steps to be taken in 2025
- From autumn 2025, countries and actors from science, business and society will be invited to co-design
Core problem: German transfer weakness A central focus is on overcoming Germany’s chronic transfer weakness – i.e. bridging the gap between research and practical application. For this purpose, new approaches in the promotion and innovation financing are to be established.
Community approach: The Agenda sees itself as a "joint design mandate" and is aimed at implementation partners from all relevant areas: Science, Economy, Society and Administration.
Economic reasoning: Federal Minister Dorothee Bär stressed the enormous leverage effect: According to the European Commission, every euro invested in research brings back up to 11 euros for the EU economy. She warns: "Those who do not invest in innovation today will be dependent tomorrow."
Philosophy: Innovations are not defined as luxury, but as Germany's business model and basis for future prosperity. The agenda is intended to bring Germany back to the forefront of international technology competition.
Source: Handelsblatt | Handelsblatt
Article 6
Citrix, that was probably nothing - Citrix Bleed 2 is about
Current status 30.6 – at least 1200 Citrix NetScaler ADC and NetScaler Gateway instances are currently unpatched on the network.
Party on, Wayne?
More than 1,200 publicly available Citrix NetScaler ADC and NetScaler Gateway devices have not yet been patched against a critical vulnerability that is considered actively exploited. The vulnerability allows attackers to bypass authentication by hijacking user sessions.
The vulnerability (CVE-2025-5777 | EUVD-2025-18497):
- Called ‘Citrix Bleed 2’, following a similar gap exploited in 2023
- Allows unauthenticated attackers to access locked storage areas
- Attackers can steal session tokens, credentials, and other sensitive data
- Even Multi-Factor Authentication (MFA) can be bypassed
Current threat situation:
- The Shadowserver Foundation Over 2,100 Vulnerable Devices Discovered
- Citrix does not confirm active usage yet
- However, cybersecurity firm ReliaQuest reports targeted attacks with medium security
- Suspicious activities include hijacked web sessions and LDAP queries for Active Directory intelligence
Recommended actions: Citrix recommends administrators patch all NetScaler devices immediately and stop all active ICA and PCoIP sessions after the update. In addition, companies should review their access controls and monitor the devices for suspicious user activity.
FunFact:
At the same time, more than 2,100 NetScaler devices are also against another critical vulnerability (CVE-2025-6543) not patched with score 9.2, which is already exploited in denial-of-service attacks.
Wow... Party on, Wayne! Party on, Garth!
Article 7
Mindfactory Resurrection: Heise takes over
Heise acquires hardware retailer Mindfactory – Key facts
The deal: The heise group takes over the hardware retailer Mindfactory as planned. The handover will take place on 31 July 2025, after which the company will be renamed heise mindfactory gmbh.
The Federal Cartel Office has given the green light.
Background of the acquisition: Medienhaus Heise took a remarkable step on 30 June 2025 and took over the entire business operations of Mindfactory GmbH. The acquisition takes place as part of an asset deal. Mindfactory was Previously in insolvency proceedings I was looking for an investor.
New leadership: Marcel Kirchner is appointed as the new Managing Director. He previously spent almost 16 years at Mindfactory in Purchasing as Purchasing Manager and holds a 3.57 percent stake in the company.
Meaning: If this happens, one of the largest German online retailers of PC components changes hands. Germany’s leading gaming retailer ‘Mindfactory’ has taken legal action against Restructuring in self-administration successfully completed.
Business strategy: The new company, which will constitute the new Commerce division alongside Content, Connect and Compare, will be officially launched on July 31, 2025.
The acquisition saves one of the most important German hardware retailers from insolvency and expands Heisse's business area to include the e-commerce sector.
Article 8
NVDA 3.7 is the most valuable company in the world for a short time
Nvidia briefly reaches the historic milestone as the most valuable company in the world.
It hasn't lasted long, but the trend is clearly recognizable.
On 3.7, Nvidia closes with a market value of 3 trillion and 920 billion – just above the previous record holder Apple, which was considered the most valuable company in the world with 3.915 trillion at the close of the market on 26.12.2024.
$4 trillion stock market value. This is almost four followed by twelve zeros – Okay, almost, put out to tender: 3920000000000 dollars. It's insane.
By the way, it was only 4 years ago when Apple was celebrated for half of this market value (2020) with the hint that they were able to double their value within only 2 years. Apparently, growth is now slowing down, or in other words, the next doubling has also taken twice the time.
Please do not take this seriously: If we extrapolate this growth from Apple's recent past to Nvidia's medium-term future, the 8 trillion target should be torn around 2033.
Updated just a week later: The chip giant Nvidia has reached a historic milestone: The first company in the world to crack on graphics cards AI hardware ⁇ specialized group the brand of $4 trillion stock market value.
$4 trillion: Nvidia's Most Valuable Company
As a result, Nvidia has become the most valuable joint stock company in the world.
The rise of Nvidia is closely linked to the boom in artificial intelligence. The company is massively benefiting from the high demand for AI hardware and graphics processors needed for machine learning and AI applications.
Nvidia is now worth more than twice as much as all 40 DAX companies combined. Nvidia was temporarily the most valuable company in the world in June and has now further expanded this position.
Ranking of the most valuable companies in the world 2025
The impressive market capitalization reflects investors' expectations that Nvidia will continue to benefit from the ongoing AI boom. The company has established itself as a leading provider of chips that are essential for AI training and inference.
Source: Reuters article
Article 9
Cisco SSH Vulnerability in CUCM
BaseScore 10/10 - Careful people! CVE-2025-20309 | EUVD-2025-21714
Cisco CVE-2025-20309 Vulnerability Summary and Update directly from the manufacturer Cisco
Product concerned: Cisco Unified Communications Manager (CUCM) Cisco, Vulnerability CVE-2025-20309 poses high risk of remote exploitation - ZAM for all Cisco Unified CM and Unified CM SME Engineering Special (ES) Versions 15.0.1.13010-1 to 15.0.1.13017-1
Type of vulnerability: The vulnerability stems from poor management of SSH access controls, allowing an unauthorized attacker to bypass established security mechanisms.
Particularly spicy: The access takes place via a developer root account with static SSH access data, which can not be changed at all. Supposedly a remnant of development. For example, in the Heise Forum, it is often assumed in such a case that this may have had little to do with accidents.
Severity: UPDATE: CVSS v3.1 Result: 8.6 (High Severity) High Risk of Remote Exploitation
Exploitation: This error can be exploited remotely by misconfiguring an SSH session without requiring prior authentication. The Vulnerability is Loud CERT-FR Already actively exploited.
Impact: A successful attack allows:
- Unauthorized system access
- Bypass network security policies
- Restoring Confidential Data
- Disruption of telephony services
Countermeasures:
- Fix via software update available in CUCM
- There is no known workable workaround
- Cisco recommends disabling SSH access when not mandatory and restricting network access
Publication: The security bulletin was published by Cisco on 2 July 2025 and reported by the French CERT-FR on 3 July 2025.
The vulnerability poses a serious threat, especially to VoIP infrastructures, as it can be used as an entry point for larger network attacks. In addition, remote attackers can access these systems completely without authentication. Afterwards, they can execute malicious code with root privileges, the absolute supergau.
Sources: nicolascoolman.eu | dfn-cert.de | cisco.com
So it was again for KW27 – this time with a clear focus on defence – I hope to read again soon.
Until then, free to Sun-Tsu:
Learn from every battle, whether won or lost
Analyze every incident, whether successfully fended off or damaging, to learn lessons and continually improve your IT defense.
This is the only way to better manage future threats.