For clarification only:
This is not a sprint, this is continuous running!
Reaching somewhere between 92 and 99% Home network security is not a one-off achievement, but a continuous process. The digital landscape is constantly evolving, new threats are emerging, and software vulnerabilities are constantly being discovered. Therefore, an attitude of constant vigilance and adaptation is essential.
The need for this continuous review and adaptation can be understood as the ‘continuous (post)calibration’ in home network security. Concepts from Quality Assurance and Lean Six Sigma, which speak of ‘continuous improvement’ and ‘regular assessment’, underline that safety is not a static state. Just as in metrology, continuous calibration ensures accuracy, so too must home network security be constantly reassessed and adjusted to keep pace with the evolution of threats.
A ‘set it and forget it’ approach is insufficient; 99% To achieve and to keep it is the motto.
Software updates are the backbone of modern security. Whether firmware, operating system, browser or app, security gaps are always discovered everywhere and regularly supplied with updates, patches, upgrades. – One or the other wonders now, aren't these all other names for the same thing? The answer is a clear jein. ⁇
- Patches:
- Fix specific bugs or security flaws.
- They are usually small and quick to install.
- Often published at short notice to address critical issues.
- Example: A patch that closes a security vulnerability in a web browser.
- Updates:
- Most often include bug fixes, performance improvements, and minor feature enhancements.
- Can be published regularly, e.g. monthly or quarterly.
- Can include both patches and new features.
- Example: An update that improves a game's performance and adds a new character.
- Upgrades:
- Represent a major version change, often from one major version to the next (e.g. from Windows 10 to Windows 11).
- May include new features, a revised user interface, and possibly performance improvements.
- They often require more planning and preparation, as they can involve major changes.
- Example: An upgrade to a new version of CAD software that offers new modeling features and an improved user interface.
Okay, so far understood – and how to proceed now, there are far too many individual places where it would have to be checked if there is something new? Yes - well. Again a clear Jein!
- Importance of Automatic Updates: Many devices and applications offer the possibility to install firmware or software updates automatically. This function should be activated. It ensures that known security vulnerabilities are closed as quickly as possible without the user having to intervene manually.
- Manual tests: Despite activated automation, it is advisable to check regularly (e.g. monthly) manually whether updates have actually been installed and whether new versions are available. This is especially important because automatic updates might not always work smoothly or be blocked by certain configurations.
- Verification of security settings: In addition to firmware updates, settings should be checked periodically. This ensures that no unwanted changes have been made (e.g. due to malware or unauthorized access) and that all security functions are still optimally configured. Logs can also help. But more on that below.
Again emphatically said: ‘Set it and forget it’ is not enough, or to put it in the words of Mark Twain:
Continuous improvement is better than delayed perfection.
Updating for lazy? Gladly!
On Windows 10 and above, there is a quite handy tool to keep installed applications, services and apps up-to-date – ‘winget’
It is accessible via the standard command line, which you can start e.g. via Windows key + Text cmd and the command below.
Alternatively, you can also find cmd in the star menu if you are looking for command line or command prompt. And if you don't want to go to the start menu, go directly to the path of the .exe %windir%\system32\cmd.exe
What also works is to write Windows key + R and "cmd".
Or Windows key +X – then choose Terminal (but then officially the PowerShell)
No matter which way you take, after that all you need is the following command:
winget upgrade --allWhen you first start, ask yourself winget if you are sure that you really want to run this application. This can then be confirmed with Y or J. After that, you can also start automatically updating the installed apps. Conveniently without user input and without overwriting your program settings, Windows updates the ‘outdated’ applications for you. In the end, should there be any leftovers that actually need to be updated by hand (which can happen), at least the main work is done.
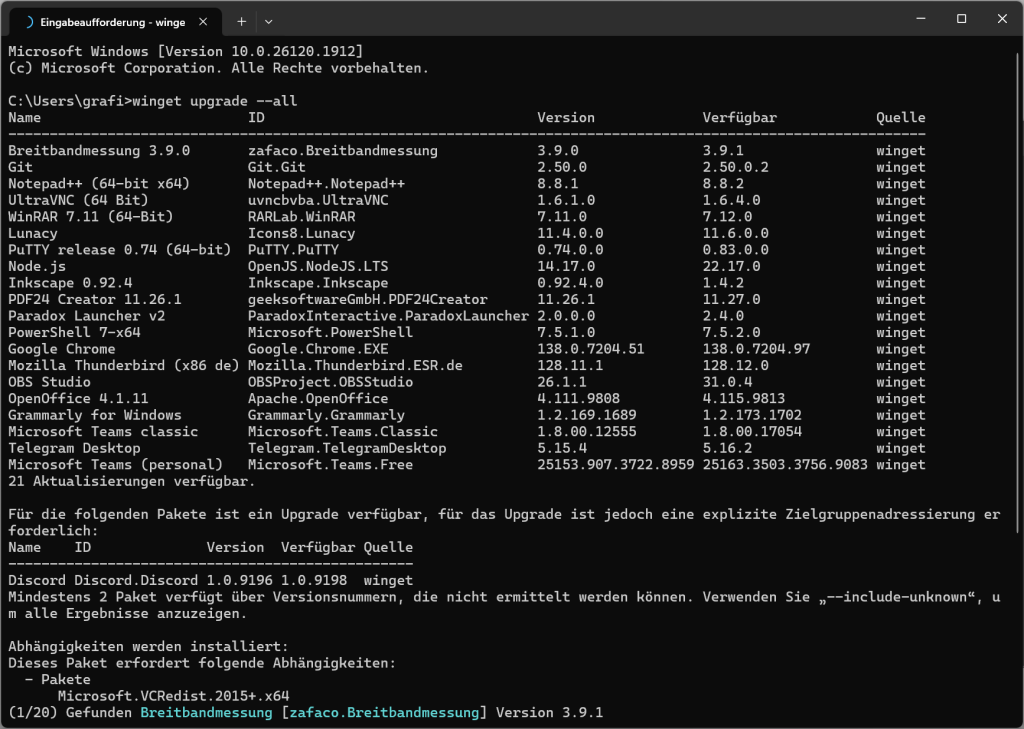
If you run this command regularly in addition to the Windows Update, you can definitely be sure that no old versions with possible security vulnerabilities on your PC will become a problem.
Disclaimer: As in previous posts, 100% There is no security, even these updates and upgrades will reduce the likelihood that a gap can be exploited but never completely prevent it!
In this sense, I say: Wooden eye stay vigilant!
Logging and anomaly detection helps
The eyes and ears of your network
Routers and firewalls log a variety of events that can provide valuable insights into network activity. Although interpreting these logs is often challenging for home users, taking an occasional look at certain patterns can help identify problems early on. In addition, one or the other can also be found out via the Windows event display. Let's take a closer look at all this.
- What you should consider in principle (for home users):
Typical alarm signs that something is wrong as follows
– Searches or pop-ups that appear suddenly
– Fans that turn up even though nothing computationally intensive is running on the PC
– Exploding ‘urgent’ warnings
– Files on the desktop that disappear or appear on their own
- What router logs can reveal: Logs contain information about configuration changes, denied access, use of security mechanisms, and potential anomalies.
- Unexpected login attempts: Multiple failed login attempts on the router interface may indicate brute force attacks.
- Unknown devices in WLAN/LAN: The list of connected devices (often with MAC addresses and IP addresses) should be checked periodically to identify unknown or suspicious devices.
- Unexplained port releases: If UPnP is or has been enabled, devices may have opened ports without the user's knowledge. A check of the port releases is advisable.
- High or unusual traffic: Sudden spikes in network traffic outside normal hours of use may indicate denial of service (DoS) attacks or malware activity.
- System errors or warnings: Messages about hardware issues, DNS errors, or connection issues can indicate underlying vulnerabilities.
Challenges for home users:
Routers and firewall logs are often technical and difficult to interpret. In addition, they are quickly overwritten on many consumer devices, which makes long-term analysis more difficult. Professional anomaly detection tools used in companies and their networks are usually not practical for home users.
level92 Recommendation: Despite the challenges, it is recommended to regularly check the logs manually for anomalies, especially after unexplained network problems or suspected unauthorized access. Many routers provide at least a simple overview of connected devices and basic events.
It's better to have automation, isn't it?
Also in the home network you can use systems that take such work off.
Already a few years ago on heise.de is a beautiful article published, which describes installation and setup in the Homelab with open source software evaluation and warning systems. What is meant by this SIEM Systems, pronounced: Security Information and Event Management
ELK
The Software modules for ELK used in this article, Elasticsearch, Logstash and Kibana Today it is a beautiful base and also a great project that Often and gladly is used.
Wazuh
An alternative system that can also be tested on a fixed basis would be Wazuh – it is a host-based intrusion detection system (HIDS), which is good for the Monitoring of endpoints ElasticStack is a more comprehensive platform for log management and analysis.
Greylog
It would also be conceivable Graylog as a central management basis for the home network logs. If you need a user-friendly and quick-to-use SIEM solution with a focus on log management and fast investigations, Graylog is the better option.
It is advisable to analyse the specific requirements and, if necessary, examine the other two solutions in detail before making a decision. Wazuh goes the fastest, ELK remains configurable in the best possible way. Greylog is in between. There are others too ⁇
Continuous improvement:
Mastering the Level 92 challenge
Home network security is an ongoing process that requires constant attention. Achieving absolute self-confidence is not even the goal, but to permanently question the idea of security.
Do not see it as a one-off task, but a continuous effort. New devices are constantly being added, new services are being used, and new threats are emerging that require constant customization.
The "Level 92" mentality means having the willingness to have the "last 10".%“ to check and optimise safety over and over again, even if the effort seems high. This continuous effort distinguishes a ‘well-protected’ from a truly ‘resilient’ home network.
Any investment in security today will pay off in the future as new technologies such as more IoT devices or more complex smart home systems are integrated into the network. The proactive maintenance of the network is an investment in one's own digital future and peace of mind.
TL:DR – There is always something to do!
The router is the undisputed foundation of your home network, your digital living space. Its careful configuration and continuous maintenance are not only a technical necessity, but an investment in your digital sovereignty and security. The same goes for other devices, services and applications. The ‘Level 92’ philosophy teaches us that the journey to optimal safety goes beyond basic attitudes. While the initial configurations are the foundation, the true, profound improvements lie in the details, often neglected out of convenience or ignorance.
These ‘last 10 %“ of the effort will have the greatest impact on the protection of your network.
Proactive measures such as the consistent application of 2FA/MFA, strategic network segmentation, and the presence of robust contingency plans are critical to turning your home network into a digital fortress. Safety is not a one-time sprint, but a marathon that requires continuous review, adjustment, and a proactive mindset. Take on the challenge of making your home network a masterpiece of security and resilience. It is an ongoing task, but it pays off in an undisturbed and protected digital everyday life.