In the digital world, password reuse is a widespread and dangerous phenomenon. It seems convenient to only have to remember one or two patterns to sign up for dozens of services. But this apparent convenience carries an enormous risk: Credential stuffing. This cyberattack takes advantage of this very human weakness and is becoming more and more effective as cybercrime becomes more professional.
What is Credential Stuffing?
Imagine using the same email address and password for your online shopping account as for your other services, especially for your online banking app. This is where credential stuffing comes in. Attackers use huge lists of stolen credentials captured in a service breach to systematically try to log in to other completely independent services.
The attackers speculate that some of the department store customers also have an account with an email service or bank and use the same credentials. With automated bots, they can perform millions of such experiments in the shortest possible time. Although the success rate per attempt is only about 0.1 percent, the sheer volume of records traded (often millions to billions of credentials) makes the attack incredibly lucrative. With a million attempts, a thousand accounts can already be cracked, and even a small part of it, which contains valuable data such as credit card information or personal data, makes the effort worthwhile for the criminals.
The thieves are not even interested in immediate success, often the information so captured is then also used to operate personalized phishing. If the attacker is aware that you are using service XYZ, he can also send you an email that is personalized and as official as possible to entice you to serve him your login data on the silver platter on a fake website.
The power of bots and the powerlessness of companies
Credential stuffing is different from traditional brute force attacks, where passwords are guessed without any clues. Instead, the attackers are already using ‘found’ data. Modern credential stuffing software is so intelligent that it bypasses traditional defense mechanisms such as IP locks and time delays. Their bots distribute the login attempts over different IP addresses and mimic legitimate traffic, so that they are hardly recognizable even for companies and their security software. Often the only sign is a slight increase in login volume, which is difficult to distinguish from normal user behavior.
The only effective protection: Unique passwords
The main reason for the success of credential stuffing attacks is that most people (according to estimates up to 85 percent!) use the same passwords or similar patterns for multiple accounts. No matter how complex your password is, if you use it multiple times, it can be cracked by credential stuffing. A strong password only protects you from brute force attacks, not from reusing stolen data.
The solution is surprisingly simple:
- Use unique passwords. A new, unique password should be created for each service. This may sound tedious, but Password manager This is the simplest and safest solution. They create and store the passwords for you, so you only need to remember a single master password.
- Enable two-factor authentication (2FA). Wherever available, use 2FA. Even if your password falls into the wrong hands, attackers will still need a second factor (e.g. a code from your smartphone) to log in.
Why Your Password Builders Are a Ticking Time Bomb
Many people think they are clever by using a sophisticated ‘build-in-the-box’ system for their passwords. The principle sounds simple at first: You take a strong, unique basic password and add the name of the service or an abbreviation at the beginning/end. For example, a basic password such as It's super secret!23 a password such as Super secret!23@Amazon or Super secret!23@PayPal. At first glance, this seems to be a safe and at the same time convenient method, since you only have to remember the basic scaffolding.
But it is precisely this strategy that is a found food for attackers. As soon as you pass through an Credential stuffing-Attack or a data leak only get their hands on one of these passwords, they know the whole system. An attacker who Super secret!23@Twitter Of course, if you have stolen, you can count 1+1 together and then you are relatively sure that you are using similar patterns for other accounts.
You will then systematically try to deal with Super secret!23@Amazon, Super secret!23@Gmail Or, even worse, Super secret!23@Sparkasse to register. The attacker doesn't even need to know which services you are registered with, the combination of your email address and the suspected password pattern is simply tried out across countless online services. And even slight modifications can be tried out so fast, 23, 24 or 25 (because you just got older) as a number would be possible ratz-fatz tried, just like the @, or the popular ! „ $ or ? as a special character.
The danger is all the more real, because leaked passwords are not always, but frighteningly often in plain text. If your password Super_Secret!23@Dropbox or Super_Secret!23@VereinXYZ Once you appear in such a list, your entire modular system is immediately unmasked. And even if these passwords are only available as a hash value, modern computer systems can still crack the partially simple encryption with justifiable effort. Specopssoft.com has tried a try with typical encryption, many services used (at least in the past) even far less secure encryptions such as MD5 or SHA-1.
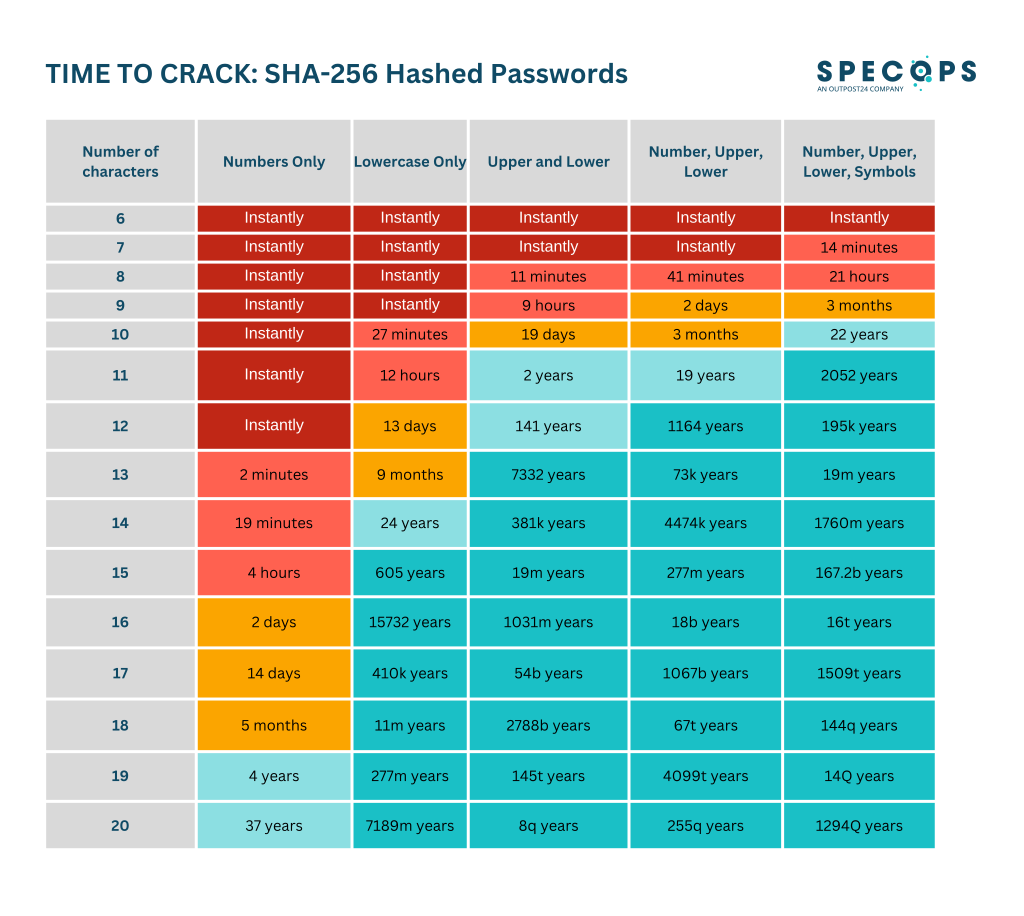
So if the basic structure of your kit is already known and you can provide some information; Let's say we expect "only 2 numbers and 1 special character", of course the whole thing goes much faster.
The initial data leak also doesn't have to have been a large, international corporation. If the admin installs a wrong plugin on a small inconspicuous website or does not regularly install security updates, such data can also be stolen from there. Attackers then simply use them in all major services and even if only One out of 10,000 If you get a hit, that's already a success and you as a victim have to clean up the shards. This approach, which is perceived as convenient and safe from the user's point of view, is actually an invitation for criminals to open the doors to your most important accounts. to direct access to your e-mails or finances.
Another typical example: The password policy states that you every X months You need to change your password. Nor can it be that you The Last 3x have already used. What does the user make of it? Password1! Password2! Password3! Password4! And when the year is over, from the comfort of course again from the front. It's a stupid idea too, sorry. :-/ Convenient, easy to remember but also just as easy to see through if any of them ever fall into the hands of the attacker.
The only really safe strategy is: Absolutely every password must be unique and At least the most important services with deposited bank data with a other method such as 2FA/MFA secured will be. A password manager and an authenticator app on your phone can help you implement this golden rule without any hassle.
haveibeenpwned.com: Self-checking for your safety
But how can you find out if your email address or passwords are already part of such a traded list? One of the most well-known and trusted points of contact on the Internet is the website haveibeenpwned.com, operated by the renowned Australian Security expert Troy Hunt. The site offers two crucial features to check your digital security:
- Verification of email addresses: You can enter your email address to see if it has appeared in known data leaks. The page will then show you which services have captured the compromised data, giving you the opportunity to immediately change your email as a login name or/and password for these services.
- Verification of passwords: Even more important is the verification of passwords. The site will then match your entered password (or email) with a database of over 15 billion login credentials stolen in the past from over 900 leaks that have become known.
Here comes the crucial point: Your input will never be transmitted to the server in plain text. Instead, a so-called hash value is formed from your password. A hash is a unique cryptographic string. The website sends only part of this hash value to the server to match it with the database of known compromised hashes. Since your actual password is never transmitted, the process is completely secure.
If your password is listed as ‘pwned’, it means that it has already appeared in a data leak in the past. You should change it immediately in this case. Regular use of haveibeenpwned.com is an essential part of checking whether the credentials you are using are already in circulation and to proactively respond to security risks.
Password managers now also offer this functionality through the bank. Using the example of Google, you will see 3 levels in the Chrome password manager: (1) passwords that are known from a leak, (2) passwords that have been used several times and also (3) generally weak passwords. These can be the usual suspects like Password123!, which at least includes upper and lower case, numbers and even a special character but also known in password lists and is therefore also tried on stupid Brute Force. But this is a completely different topic. ⁇
Organizations can protect themselves with dedicated bot management services that detect and block suspicious traffic, but the strongest protection is in the hands of each individual. As long as we continue the practice of password reuse, credential stuffing remains one of the biggest threats in the digital world. Protect yourself now and take the first step by changing your most important passwords to individual ones without patterns and – to keep track – using a password manager.
Update for August: Okay, you don't trust a password manager because it's there in the past Have there been burglaries? Then a self-hosted instance that only runs locally in your home network and airgapped or only allows external VPN access could be an alternative. Vaultwarden would be an idea, I also wrote an article about it.
Is it too complicated for you? Even a password-protected list of your new, individual passwords would be better than your building block. Two-factor auth also regulates. Honestly! Or Switch to Passkeys!